Exploring the Security Dynamics of Decentralized Autonomous Organizations (DAOs)
Decentralized Autonomous Organizations (DAOs) have emerged as a groundbreaking concept, allowing communities to govern themselves through decentralized decision-making processes. As the popularity of DAOs grows, ensuring the security of these autonomous entities becomes paramount for maintaining trust and reliability in the decentralized landscape.
The Essence of DAOs in Decentralization
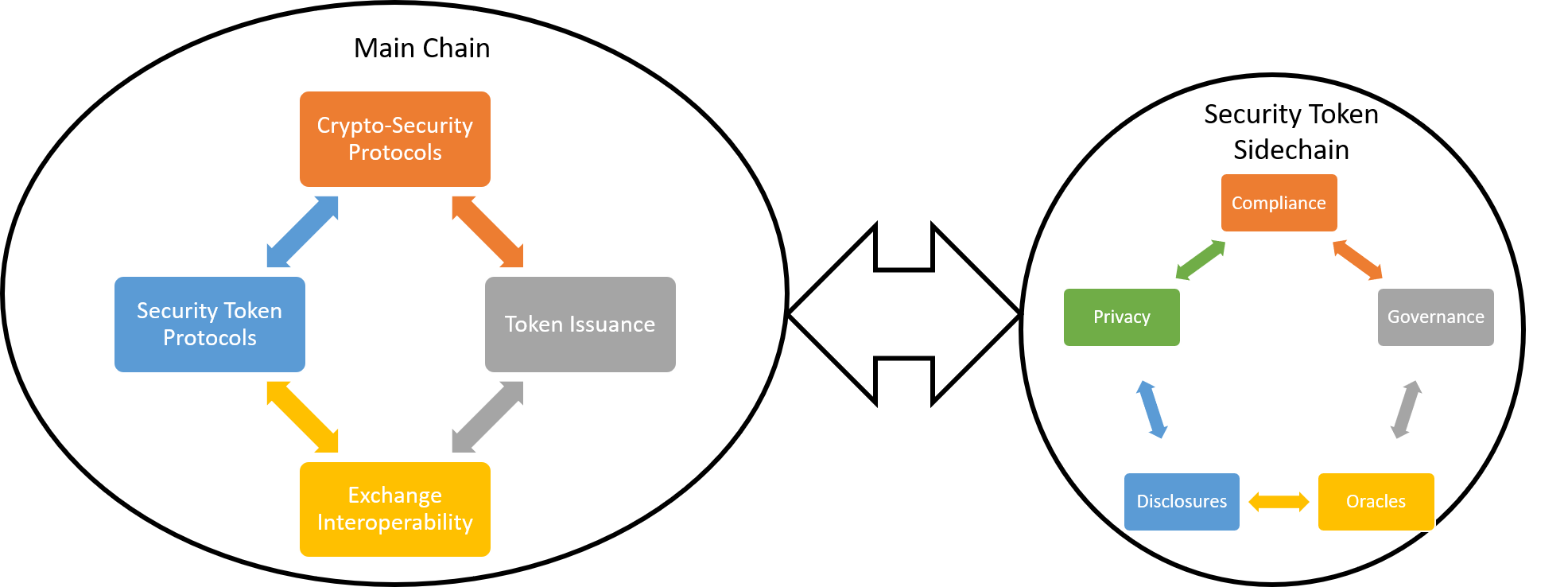
DAOs represent a shift in organizational structure, leveraging blockchain technology to enable decentralized decision-making. These entities operate through smart contracts, allowing members to vote on proposals and influence the direction of the organization without the need for centralized control. This model fosters inclusivity and transparency within communities.
Security Challenges in DAO Ecosystem
Despite the promise of decentralized governance, DAOs face unique security challenges. Smart contract vulnerabilities, governance attacks, and potential exploits require comprehensive security measures to safeguard the assets and decision-making processes of DAOs. Ensuring the security of these entities is essential for fostering confidence among their members.
Smart Contract Audits: A Foundation of Security
Security in DAOs begins with robust smart contract audits. Reputable DAO platforms conduct thorough audits by independent firms to identify and address vulnerabilities in the code. These audits serve as a foundational element, providing assurance to members that the smart contracts governing the DAO have undergone rigorous scrutiny.
Transparent Governance for Trust
Secure DAOs prioritize transparent governance structures to instill trust among members. Openly sharing information about decision-making processes, fund allocations, and project developments enhances transparency. Transparent governance not only ensures accountability but also empowers members to actively participate in shaping the future of the DAO.
Mitigating Risks through Decentralized Decision-Making
One of the inherent strengths of DAOs is decentralized decision-making. This not only distributes power among members but also mitigates the risk of single points of failure. Secure DAOs leverage the collective intelligence of their community, making decisions that reflect the diverse perspectives and interests of their members.
Community Involvement and Security
Community involvement is a key aspect of security in DAOs. Platforms that actively engage their community through voting, discussions, and feedback mechanisms create an environment where potential security concerns can be identified and addressed collaboratively. Community-driven security enhances the resilience of DAOs.
Secure DAOs: A Link to Confidence
For those navigating the decentralized landscape, Secure Decentralized Autonomous Organizations (DAOs) serve as a link to confidence. These platforms prioritize advanced security measures, transparent governance, and robust risk mitigation strategies, empowering members to participate in decentralized decision-making with peace of mind.
Educating Members for Enhanced Security Awareness
Educating DAO members about security best practices is crucial for maintaining a secure environment. Secure DAO platforms provide resources and information to help members understand the potential risks, how to interact safely with smart contracts, and contribute to the overall security of the organization.
Innovations in DAO Security
As the decentralized landscape evolves, so do innovations in DAO security. From exploring new consensus mechanisms to integrating decentralized identity solutions, DAOs are continuously pushing the boundaries to enhance the security and reliability of their governance models.
In conclusion, the rise