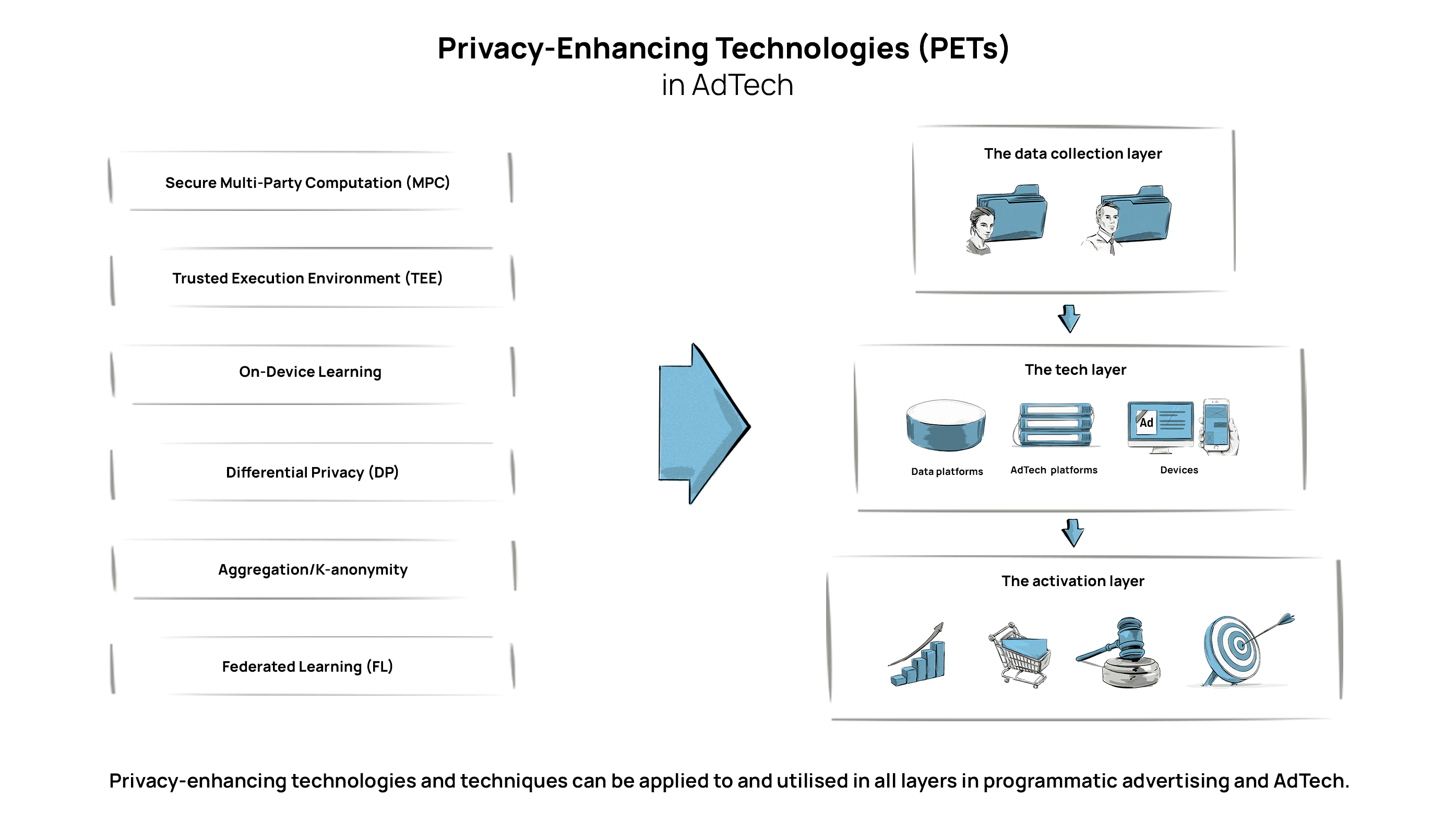
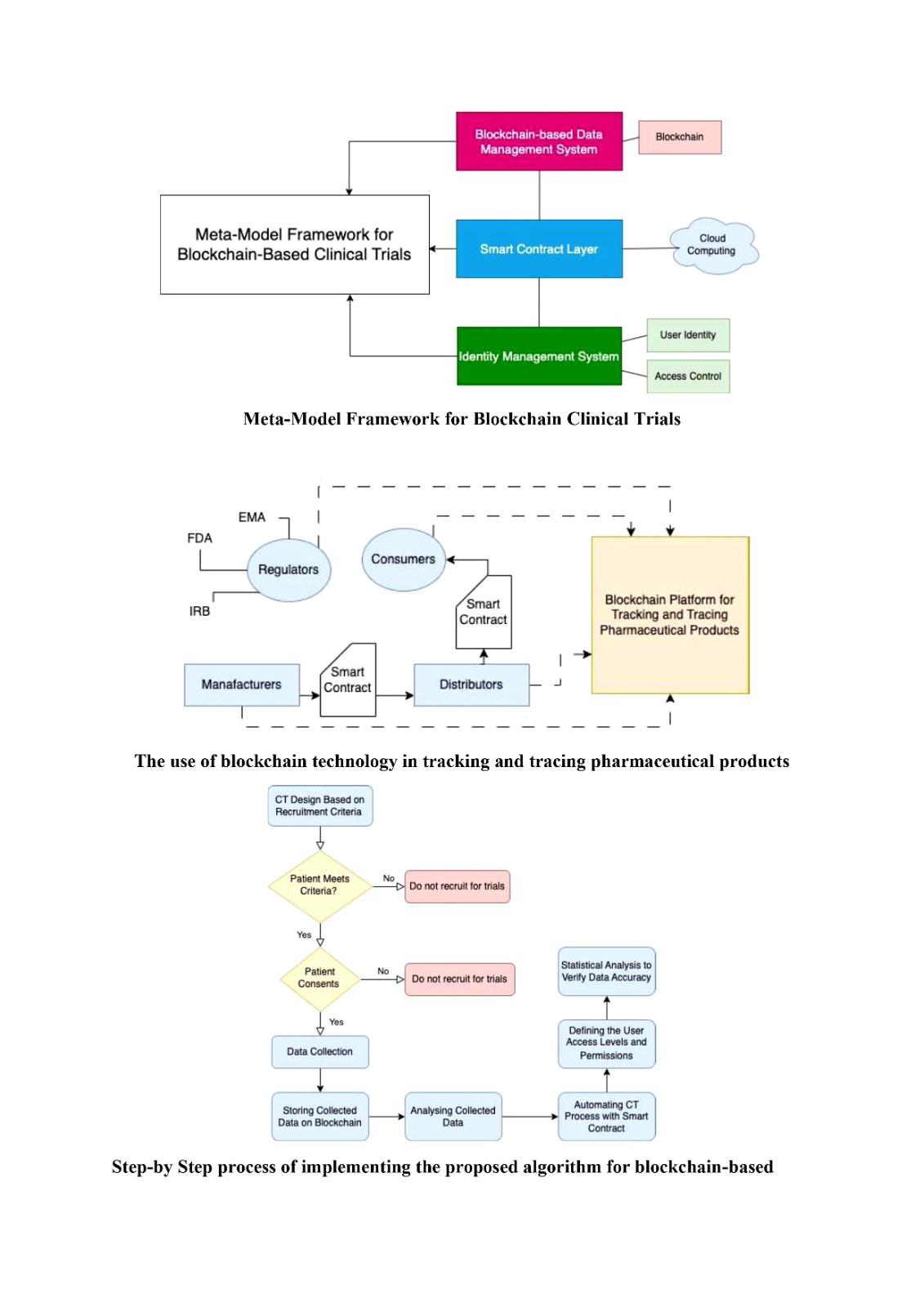
Elevating Gaming Security: The Age of Secure Blockchain Games
In the dynamic world of gaming, the integration of blockchain technology is ushering in a new era of security and innovation. This article delves into the significance of secure blockchain gaming, exploring how this marriage of technologies is reshaping the gaming landscape and offering players unprecedented levels of security and ownership.
Decentralization and Player Empowerment
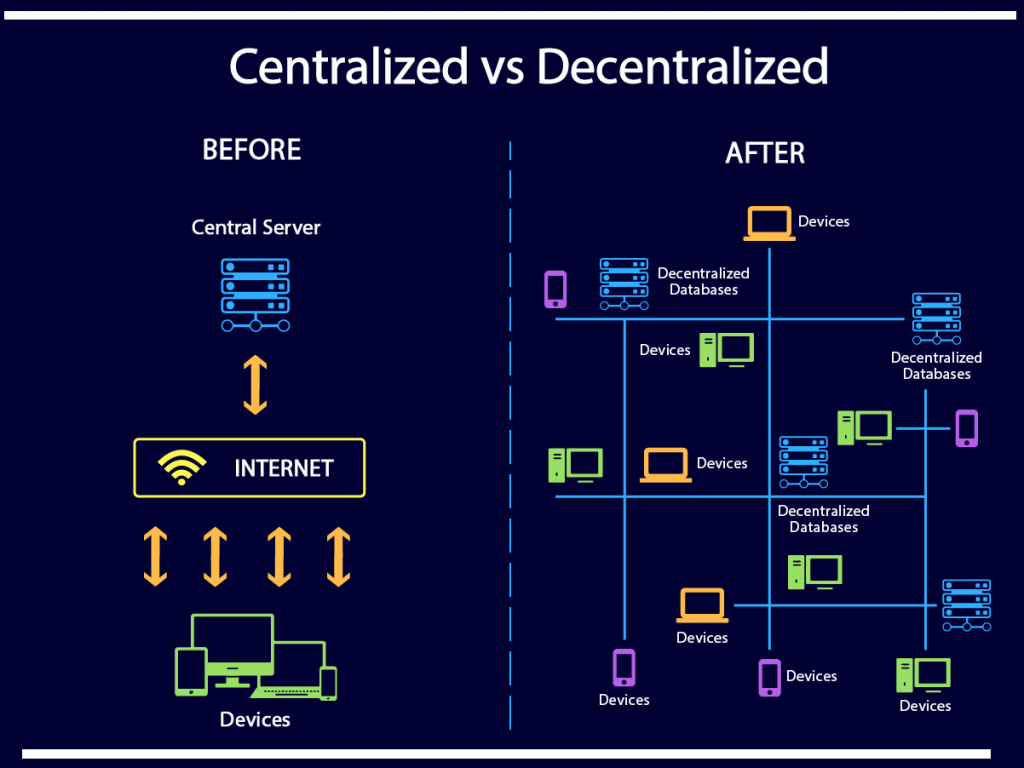
Blockchain technology introduces decentralization to gaming, shifting away from the traditional model of centralized control. Secure blockchain gaming empowers players by providing them with true ownership of in-game assets. Through blockchain’s transparent and immutable ledger, players have irrefutable proof of ownership, ensuring the security of their digital assets.
Securing In-Game Transactions with Smart Contracts
Smart contracts play a central role in ensuring the security of transactions within blockchain games. These self-executing contracts automate the execution of predefined rules, eliminating the need for intermediaries. In secure blockchain gaming, smart contracts enable trustless transactions, ensuring that in-game exchanges are secure, transparent, and verifiable.
Preventing Fraud and Cheating
Blockchain’s tamper-resistant nature is a powerful tool in preventing fraud and cheating in online gaming. Secure blockchain gaming environments leverage the transparency and immutability of the blockchain to create fair and cheat-proof ecosystems. This ensures a level playing field for all participants and enhances the overall integrity of online gaming experiences.
True Ownership of Digital Assets
Traditionally, players had limited control over their in-game assets, often subject to the rules and policies of game developers. Secure blockchain gaming revolutionizes this by granting players true ownership of their digital assets. These assets, represented as non-fungible tokens (NFTs), can be transferred between games or even traded in external markets, providing players with a new level of autonomy.
Enhanced Security for In-Game Payments
Insecure payment systems have been a concern in the gaming industry. Secure blockchain gaming addresses this by providing a secure and efficient payment infrastructure. Cryptocurrencies or blockchain-based tokens facilitate in-game transactions, reducing the risk of payment fraud and ensuring that players’ financial information remains secure.
Building Community Trust through Transparency
Trust is a critical component of any gaming community. Blockchain’s transparency fosters trust by allowing players to verify the fairness of game mechanics and the distribution of rewards. The transparent and auditable nature of blockchain transactions builds a sense of trust among players, enhancing the overall gaming experience.
Interoperability and Cross-Game Experiences
Secure blockchain gaming opens the door to interoperability, allowing assets and progress to move seamlessly across different games and platforms. This cross-game interoperability enhances player experiences by creating a unified gaming ecosystem. Players can carry their achievements and assets from one blockchain game to another, fostering continuity and engagement.
Regulatory Compliance and Legitimacy
As blockchain gaming gains popularity, regulatory compliance becomes a focal point. Secure blockchain gaming platforms adhere to regulatory standards, ensuring legitimacy and compliance with laws governing the gaming industry. This commitment to compliance not only protects players but also contributes to the overall acceptance and mainstream adoption of blockchain gaming.
Innovation and the Future of Secure