Mastering Security: The Essence of Secure Smart Contract Development
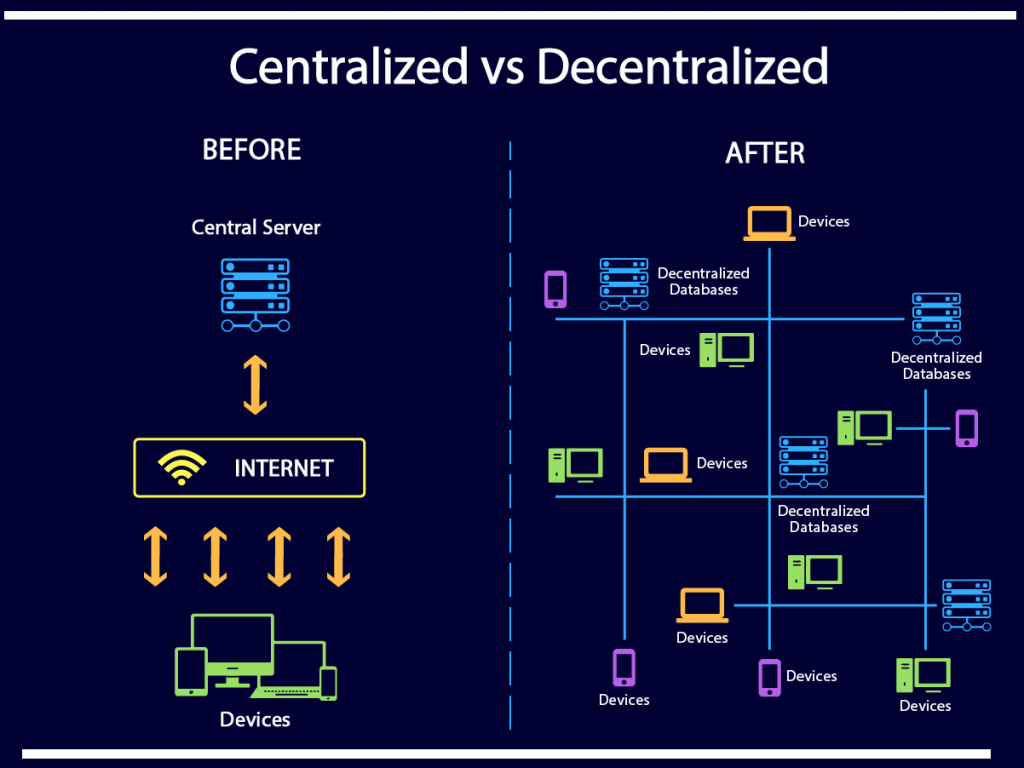
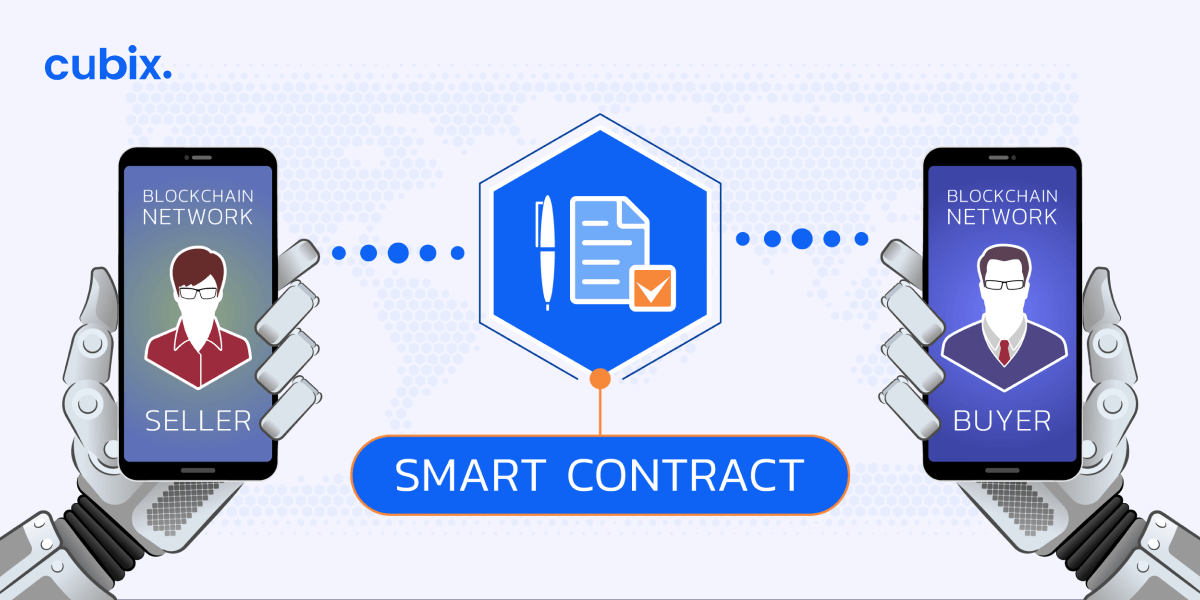
Smart contracts, the self-executing contracts with coded terms, are the backbone of decentralized applications. Ensuring their security is paramount, and secure smart contract development practices are fundamental in building robust and trustworthy decentralized systems.
Understanding the Importance of Secure Smart Contract Development
Secure smart contract development is not just a best practice; it’s a necessity in the decentralized landscape. As the digital agreements that govern transactions and processes, smart contracts must be crafted with meticulous attention to security to prevent vulnerabilities that could lead to exploitation.
Coding with Security in Mind
Developers engaged in smart contract development must prioritize security from the outset. This involves adopting secure coding practices, carefully validating inputs, and employing techniques to prevent common vulnerabilities. A proactive approach during the coding phase sets the foundation for a secure smart contract.
Thorough Testing for Robustness
Testing is a critical phase in secure smart contract development. Rigorous testing helps identify and address potential vulnerabilities and bugs. This includes both unit testing, where individual components are tested, and integration testing, which evaluates the interaction of different components to ensure the overall functionality and security of the smart contract.
Security Audits: A Critical Step
Conducting security audits is a crucial step before deploying any smart contract. Security audits involve a comprehensive review of the smart contract’s code by independent experts. The goal is to identify and rectify potential vulnerabilities, ensuring the smart contract is resilient to attacks and secure for real-world use.
Transparent Governance for Trust
Transparent governance is integral to secure smart contract development. Openly sharing information about the development process, codebase, and security measures instills trust in users and stakeholders. Transparent governance demonstrates a commitment to accountability and allows the community to participate in the decision-making process.
Continuous Monitoring and Updating
Security is an ever-evolving landscape, and secure smart contract development requires continuous monitoring. Developers should stay vigilant for emerging threats and promptly update smart contracts to address new vulnerabilities or implement improved security measures. Regular updates ensure that smart contracts remain robust over time.
Developer Education and Best Practices
Educating developers about the intricacies of secure smart contract development is vital. Establishing best practices, sharing knowledge about common pitfalls, and providing resources on secure coding contribute to a more informed and security-conscious developer community. Developer education is a proactive measure to prevent security breaches.
Building Confidence with Secure Smart Contract Development
For projects prioritizing security, engaging in secure smart contract development practices serves as a link to confidence. Platforms that invest in security measures and adhere to best practices, such as those outlined at Secure Smart Contract Development, demonstrate a commitment to building trustworthy decentralized systems.
Collaboration and Community Involvement
Secure smart contract development is not just the responsibility of individual developers; it’s a collaborative effort. Community involvement, bug bounty programs, and open collaboration contribute to a more resilient and secure ecosystem. Engaging the community in the development process enhances the collective intelligence working towards security goals.