Advancing Security: The Power of Biometric Authentication
In the ever-evolving landscape of digital security, Biometric Authentication has emerged as a groundbreaking technology, offering a more secure and convenient way to verify identities. Let’s delve into the intricacies of biometric authentication and explore how it is reshaping the future of secure access.
Understanding Biometric Authentication
Biometric authentication involves the use of unique biological traits to verify the identity of an individual. These traits can include fingerprints, facial features, iris patterns, voice recognition, and even behavioral characteristics. Unlike traditional authentication methods such as passwords or PINs, biometrics offers a highly personalized and virtually unforgeable means of identification.
Fingerprint Recognition: A Personal Touch
Among the various biometric methods, fingerprint recognition stands out as one of the most widely adopted. Each person’s fingerprint is unique, making it an ideal candidate for authentication. Biometric systems capture and analyze the ridges and valleys of fingerprints, creating a secure and efficient means of identity verification.
Facial Recognition: Seeing is Believing
Facial recognition technology has gained prominence in recent years, thanks to advancements in artificial intelligence. By analyzing facial features and patterns, this biometric method enables quick and accurate identification. It is increasingly used in applications ranging from unlocking smartphones to enhancing security in public spaces.
Iris Scanning: The Window to Identity
Iris scanning involves capturing the unique patterns in the colored part of the eye. The intricate details of the iris provide a highly secure form of biometric authentication. While less common than fingerprint or facial recognition, iris scanning offers a non-intrusive and reliable means of identity verification.
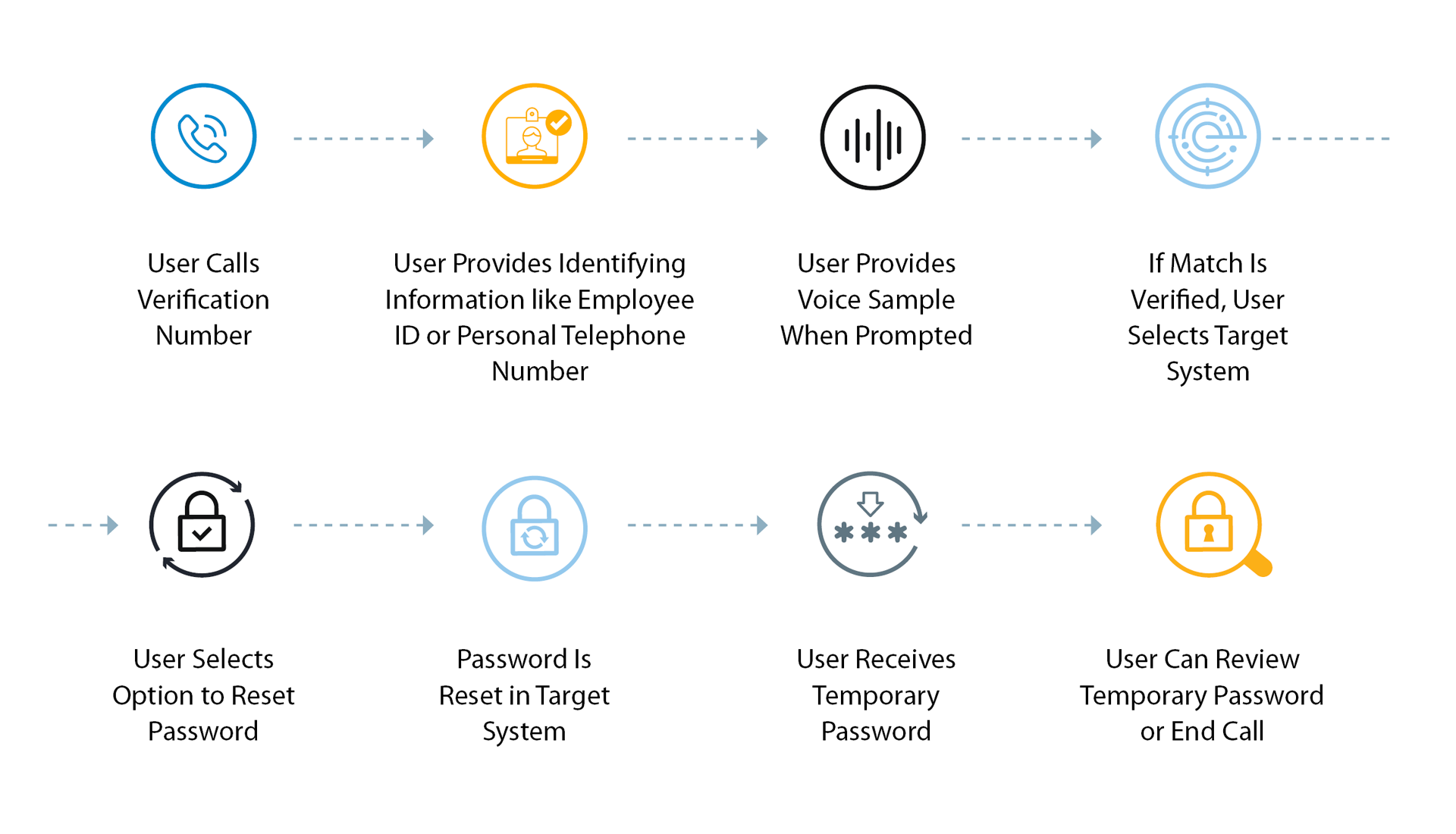
Voice Authentication: The Sound of Security
Voice recognition technology analyzes the unique characteristics of an individual’s voice, such as pitch, tone, and rhythm. This biometric method is often employed in phone-based authentication systems and voice-controlled devices. It provides a natural and convenient way to verify identity without the need for physical interaction.
Behavioral Biometrics: Your Unique Signature
Behavioral biometrics focus on individual patterns of behavior, such as keystroke dynamics, gait analysis, or even the way a person holds their device. These unique behavioral traits add an extra layer of security, as they are difficult for impostors to mimic. Behavioral biometrics are particularly effective in continuous authentication scenarios.
Biometrics and Cybersecurity
The adoption of biometric authentication has significantly strengthened cybersecurity measures. Traditional authentication methods, like passwords, are vulnerable to hacking and unauthorized access. Biometrics, being based on unique physical or behavioral traits, significantly reduces the risk of identity theft and unauthorized entry.
Enhancing User Experience with Biometrics
Biometric authentication not only fortifies security but also enhances user experience. Users no longer need to remember complex passwords or worry about forgetting PINs. With biometrics, the authentication process becomes seamless, quick, and user-friendly, contributing to a positive overall digital experience.
Challenges and Considerations
While biometric authentication offers numerous advantages, it is not without challenges. Privacy concerns, potential vulnerabilities, and the need for standardized protocols are areas that researchers and industry experts continue to address. As the technology evolves, ensuring a balance between


