Securing the Future: Quantum-Resistant Cryptography
In an era marked by technological advancements, the rise of quantum computing poses a unique challenge to traditional cryptographic methods. As quantum computers continue to evolve, the vulnerability of current encryption standards becomes apparent. Enter Quantum-Resistant Cryptography, a groundbreaking approach to fortifying our digital security against the impending quantum threat.
Understanding the Quantum Menace
Quantum computers, with their ability to perform complex calculations exponentially faster than classical computers, have the potential to crack widely used encryption algorithms. This includes those that safeguard sensitive data in finance, healthcare, and communication. The looming threat of quantum decryption has led to the development of quantum-resistant cryptography, an innovative solution to counteract these vulnerabilities.
The Achilles’ Heel of Current Cryptography
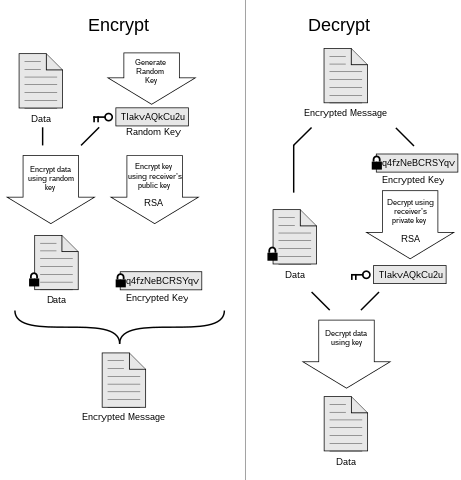
Conventional cryptographic algorithms, such as RSA and ECC, rely on the difficulty of certain mathematical problems for their security. However, quantum computers can efficiently solve these problems using algorithms like Shor’s algorithm, rendering these encryption methods obsolete. Recognizing this vulnerability, researchers have intensified efforts to create cryptographic systems resistant to quantum attacks.
Quantum-Resistant Cryptography: A Shield Against Quantum Threats
The primary goal of quantum-resistant cryptography is to design algorithms that remain secure even in the face of quantum computing power. These cryptographic systems often leverage mathematical problems that are currently believed to be hard for both classical and quantum computers. By adopting these quantum-resistant algorithms, organizations can future-proof their security infrastructure against the evolving landscape of computational technology.
Post-Quantum Cryptography Standards
In response to the urgency of the quantum threat, standardization bodies and organizations worldwide are actively working on defining post-quantum cryptography standards. These standards aim to provide guidelines for implementing quantum-resistant algorithms across various industries. Staying informed about these evolving standards is crucial for businesses and individuals looking to stay ahead in the realm of digital security.
Transition Challenges and Solutions
While the development of quantum-resistant cryptography is promising, transitioning from current cryptographic standards poses challenges. Implementing new algorithms requires careful planning, testing, and collaboration within the cybersecurity community. Additionally, organizations must consider backward compatibility to ensure a seamless transition while maintaining the security of existing systems.
Quantum-Resistant Cryptography in Action
To visualize the practicality of quantum-resistant cryptography, consider a scenario where sensitive financial transactions are secured using quantum-resistant algorithms. The link between the sender and receiver is fortified against potential quantum attacks, ensuring the confidentiality and integrity of the transmitted data. This level of security is crucial in the digital landscape, where financial transactions are the lifeblood of the global economy.
The Role of Awareness and Education
As quantum-resistant cryptography gains traction, awareness and education play pivotal roles in its successful adoption. Businesses and individuals must understand the implications of quantum computing on digital security and stay informed about the latest advancements in quantum-resistant algorithms. This proactive approach ensures a smoother transition and strengthens the overall resilience of our digital infrastructure.
Looking Towards a Quantum-Resistant Future
In the grand scheme of digital evolution, quantum-resistant cryptography stands as a beacon of hope. It represents a collective effort to