Exploring the Dynamics of Proof-of-Work (PoW) in Blockchain
In the realm of blockchain technology, Proof-of-Work (PoW) stands as a foundational concept, playing a pivotal role in ensuring the security and consensus mechanisms of various blockchain networks. This article delves into the intricacies of PoW, its mechanisms, and its impact on the broader blockchain ecosystem.
Understanding Proof-of-Work:
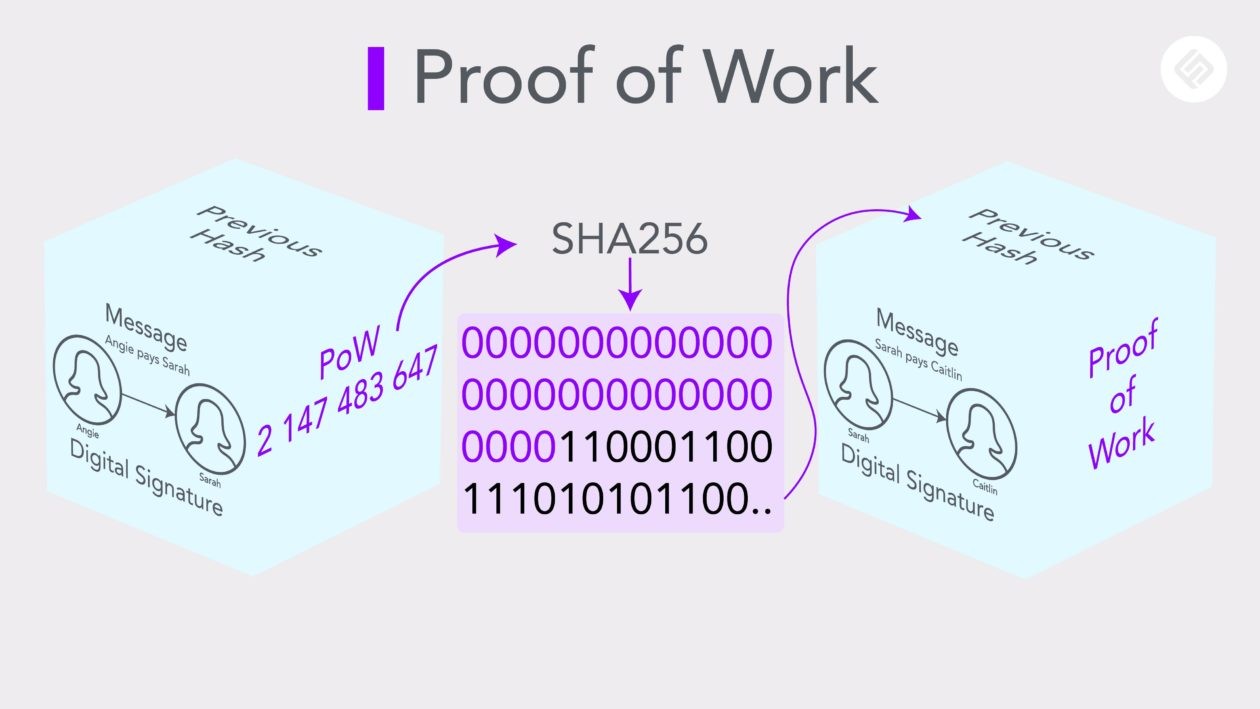
At its essence, Proof-of-Work is a consensus algorithm utilized by blockchain networks to validate and confirm transactions. It requires participants, known as miners, to solve complex mathematical puzzles as a way to demonstrate their commitment to the network. The first miner to solve the puzzle is granted the opportunity to add a new block to the blockchain.
The Mechanics of PoW:
The process of Proof-of-Work involves miners competing to find a specific value, often referred to as a nonce, that, when hashed with the block’s data, produces a hash that meets certain criteria. This process requires significant computational power and energy, making it a resource-intensive task. The intentional difficulty of these puzzles ensures that the process takes time and effort, contributing to the security of the network.
Ensuring Network Security:
One of the primary purposes of PoW is to enhance the security of blockchain networks. The computational work required to solve the puzzles acts as a deterrent to malicious actors attempting to manipulate or compromise the system. The decentralized nature of PoW, with multiple miners competing, adds an extra layer of security, making it exceedingly challenging for any single entity to control the network.
Consensus through PoW:
Consensus mechanisms are crucial for ensuring that all participants in a blockchain network agree on the validity of transactions. PoW serves as a robust consensus mechanism by requiring miners to invest time and resources in solving puzzles. Once a miner successfully solves the puzzle and adds a block to the chain, the rest of the network acknowledges the validity of the transactions within that block.
Energy Consumption Debate:
While PoW has proven effective in securing blockchain networks, it has also been subject to criticism due to its high energy consumption. The computational power required for mining has led to concerns about environmental impact. However, ongoing discussions within the industry aim to explore and implement more sustainable alternatives, such as transitioning to Proof-of-Stake (PoS) consensus mechanisms.
In the evolving landscape of blockchain technology, staying informed is essential. Proof-of-Work (PoW) is an invaluable resource for those seeking a deeper understanding of PoW and its implications on blockchain networks. The platform provides insights, guides, and resources for both beginners and seasoned enthusiasts.
The Role of Incentives in PoW:
To motivate miners to contribute their computational power to the network, PoW introduces incentives. Successful miners are rewarded with newly minted cryptocurrency coins, adding to the overall supply. These incentives not only compensate miners for their efforts but also contribute to the decentralized distribution of the cryptocurrency.
PoW in the Cryptocurrency Ecosystem:
Proof-of-Work has been integral to the development and success of various cryptocurrencies, including Bitcoin, the pioneering cryptocurrency that introduced PoW.