Navigating the Landscape of Secure Blockchain Lending
The integration of blockchain technology into lending practices has opened up new possibilities in the financial sector. This article explores the significance of ensuring security in blockchain lending, examining the key factors that contribute to a robust and trustworthy lending ecosystem.
Understanding Blockchain Lending
Blockchain lending involves the use of decentralized and transparent ledgers to facilitate loans. This innovative approach brings efficiency, transparency, and accessibility to the lending process. However, with these advantages come the imperative need for security measures to safeguard the interests of both lenders and borrowers.
Smart Contract Security
Smart contracts play a pivotal role in blockchain lending by automating and executing the terms of the loan. Ensuring the security of these contracts is paramount to prevent vulnerabilities that could be exploited. Regular audits, code reviews, and adherence to best practices in smart contract development contribute to a secure foundation for blockchain lending platforms.
Decentralization for Risk Mitigation
Decentralization is a key feature that distinguishes blockchain lending from traditional lending systems. By distributing control across the network, the risk of a single point of failure is mitigated. Decentralized lending platforms reduce vulnerabilities associated with centralized authority, enhancing the overall security of the lending process.
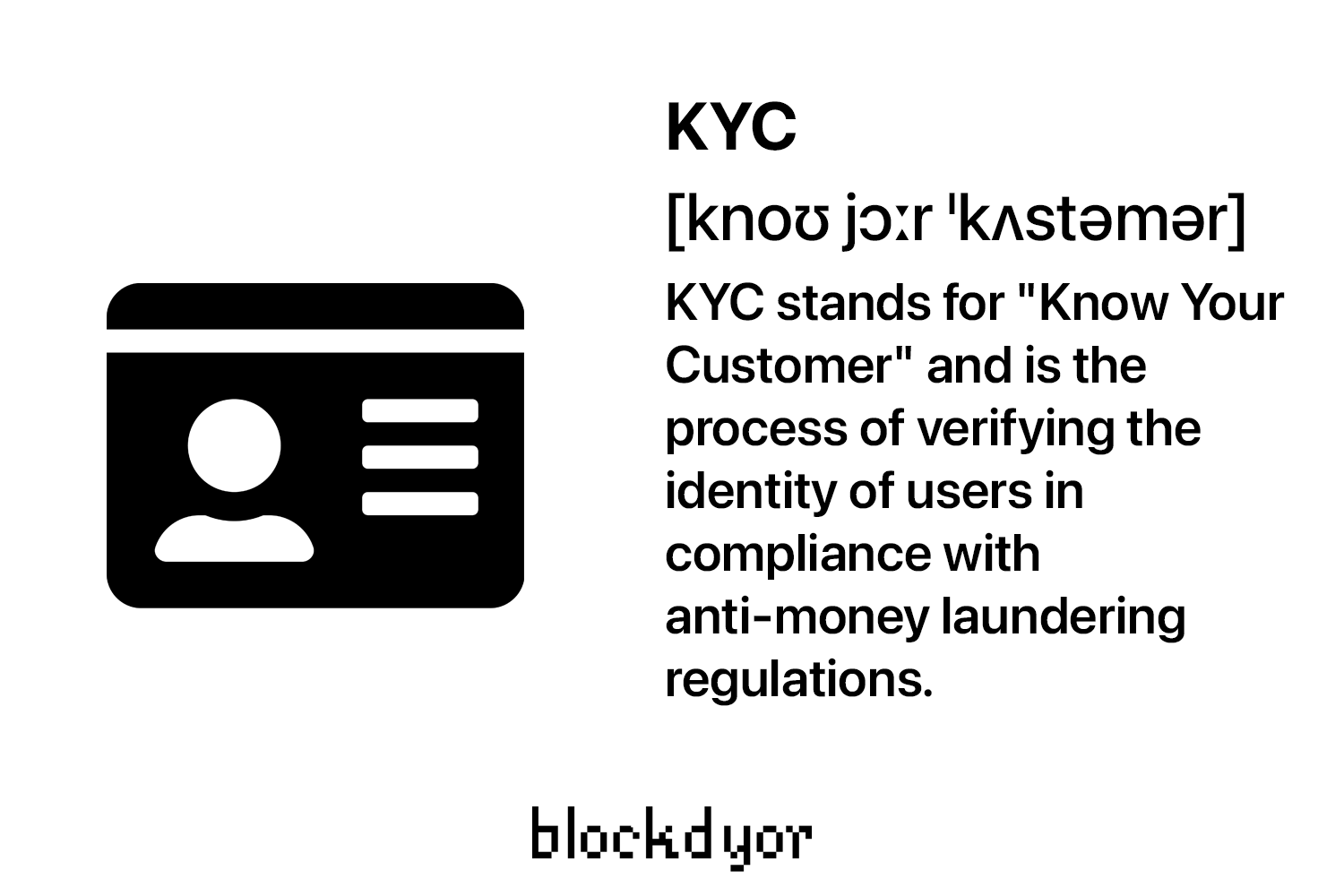
Secure Identity Verification
One of the challenges in lending is identity verification. Blockchain provides a secure solution by offering decentralized identity verification. Implementing robust identity verification protocols ensures that lenders can trust the identity of borrowers, contributing to a more secure lending environment.
Collateralization and Asset Security
Many blockchain lending platforms incorporate collateralization to mitigate risks. Borrowers provide collateral, often in the form of cryptocurrency, which is held in smart contracts until the loan is repaid. This collateralization adds an extra layer of security, reducing the risk of default and ensuring lenders have a means of recourse.
Data Encryption and Privacy
Protecting sensitive borrower information is crucial for secure lending on the blockchain. Utilizing encryption techniques ensures that personal and financial data remains confidential. Privacy-focused blockchain solutions contribute to creating a trustworthy environment where users can engage in lending transactions with confidence.
Regulatory Compliance in Blockchain Lending
As the blockchain lending landscape evolves, adherence to regulatory frameworks becomes essential. Platforms facilitating blockchain lending should actively collaborate with regulatory bodies to ensure compliance. Regulatory compliance not only enhances security but also promotes broader acceptance and integration within the traditional financial system.
Real-Time Monitoring and Anomaly Detection
Implementing real-time monitoring tools is crucial for identifying and addressing potential security threats promptly. Anomaly detection mechanisms contribute to a proactive security stance, allowing lending platforms to respond swiftly to any irregularities, thus maintaining a secure environment for both lenders and borrowers.
User Education: Empowering Participants
Educating users about secure lending practices on the blockchain is fundamental. Providing clear guidelines, educational resources, and tutorials ensures that participants are well-informed about the lending process and security measures. Empowered users contribute to a more secure and resilient blockchain lending ecosystem.
The Future of Secure Blockchain Lending
In conclusion, the integration of security measures