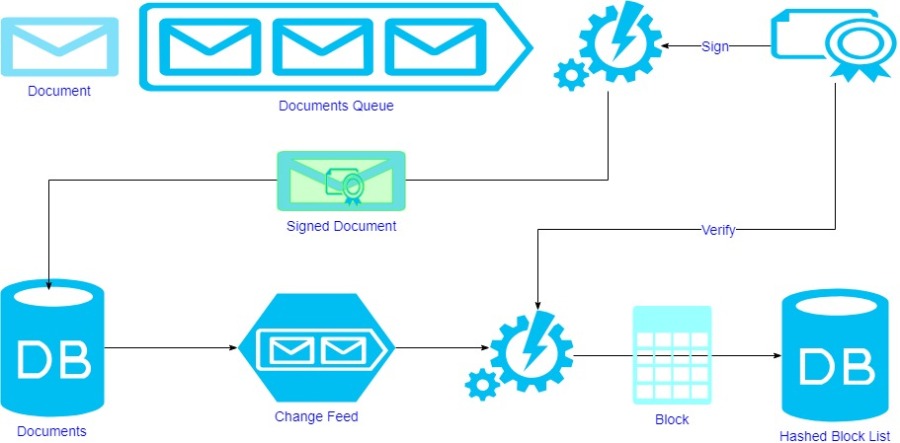
Ensuring Unalterable Data Integrity with Immutable Audit Trails
In the realm of data management, the concept of immutable audit trails has emerged as a critical safeguard, ensuring the integrity and transparency of digital records. This article explores the significance of immutable audit trails and their role in maintaining unalterable data integrity.
The Foundation of Immutable Audit Trails
At its core, an immutable audit trail is a chronological record of events or changes made to a dataset. The term “immutable” emphasizes that once a record is added to the trail, it cannot be modified or deleted. This foundational characteristic is crucial for establishing a trustworthy and tamper-proof history of data activities.
Preventing Data Tampering and Fraud
Immutable audit trails act as a powerful deterrent against data tampering and fraudulent activities. In traditional systems, malicious actors may attempt to alter or erase traces of unauthorized access or changes. With immutable audit trails, every action is permanently recorded, providing a transparent and unforgeable history of data modifications.
Enhancing Data Accountability and Transparency
One of the key benefits of immutable audit trails is the enhancement of data accountability and transparency. Organizations can trace every modification back to its origin, holding individuals or systems accountable for their actions. This not only discourages malicious behavior but also fosters a culture of responsibility within an organization.
Blockchain Technology and Immutable Audit Trails
Blockchain, the technology behind cryptocurrencies, has significantly contributed to the advancement of immutable audit trails. In a blockchain-based system, each block contains a cryptographic hash of the previous block, creating an unbroken chain of records. This design ensures that once a block is added, it becomes practically impossible to alter any preceding data, providing a high level of security.
Securing Sensitive Information in Healthcare
In sectors where the integrity of data is paramount, such as healthcare, immutable audit trails play a crucial role. Patient records, treatment histories, and other sensitive information must be protected from unauthorized access and tampering. Immutable audit trails provide a robust solution, offering a transparent and unchangeable record of all interactions with patient data.
Immutable Audit Trails in Financial Transactions
The financial sector also benefits significantly from immutable audit trails. Ensuring the integrity of financial transactions is vital for regulatory compliance and building trust with customers. Immutable audit trails enable financial institutions to maintain an accurate and unalterable record of all financial activities, reducing the risk of fraud and ensuring compliance with industry standards.
Challenges and Considerations
While immutable audit trails offer substantial advantages, there are challenges to consider. Implementing and managing such systems require careful planning and consideration of factors like storage capacity, accessibility, and regulatory compliance. Organizations must strike a balance between security and practicality in deploying immutable audit trail solutions.
Future Outlook and Innovations
As technology continues to evolve, so do the methods of ensuring immutable audit trails. Innovations in cryptography, decentralized systems, and advanced record-keeping techniques contribute to the ongoing improvement of data integrity solutions. The future promises even more robust and efficient ways to secure digital


