Empowering Digital Security with Samsung Blockchain Keystore
The Evolution of Digital Transactions
In today’s interconnected world, digital transactions have become a cornerstone of modern life. From online shopping to financial transactions, the ability to securely transfer digital assets is paramount. With the rise of blockchain technology, companies like Samsung are revolutionizing the way we approach digital security.
Introducing Samsung Blockchain Keystore
Samsung Blockchain Keystore is a cutting-edge platform designed to enhance the security of digital transactions. Built on blockchain technology, this innovative solution provides users with a secure and decentralized way to manage their digital assets. Whether it’s cryptocurrencies, digital identities, or other sensitive data, Samsung Blockchain Keystore offers a comprehensive solution for safeguarding digital assets.
Securing Your Digital Assets
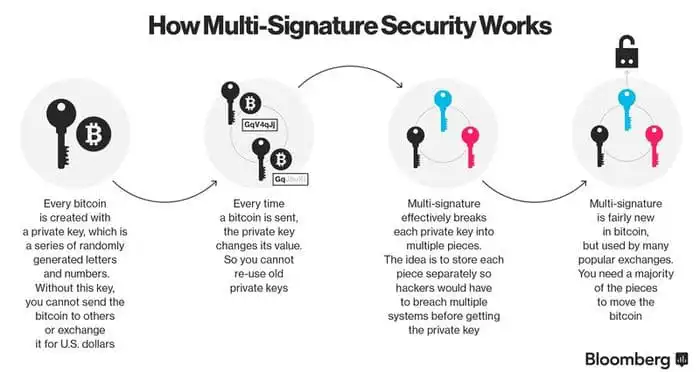
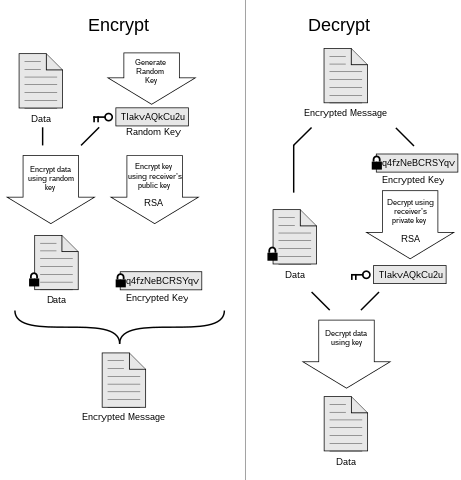
One of the primary benefits of Samsung Blockchain Keystore is its ability to securely store digital assets. By leveraging blockchain technology, Samsung ensures that users’ assets are protected from unauthorized access and tampering. With features such as encryption and decentralized storage, Samsung Blockchain Keystore provides users with peace of mind knowing that their digital assets are safe and secure.
Streamlining Digital Transactions
In addition to security, Samsung Blockchain Keystore also streamlines digital transactions. By providing a seamless and intuitive user experience, Samsung makes it easy for users to engage in digital transactions with confidence. Whether it’s sending cryptocurrencies or verifying digital identities, Samsung Blockchain Keystore simplifies the process, making it accessible to users of all levels of expertise.
Enhancing Privacy and Transparency
Privacy and transparency are essential components of any digital transaction. With Samsung Blockchain Keystore, users can rest assured that their transactions are private and secure. By leveraging blockchain technology, Samsung ensures that transactions are immutable and transparent, providing users with a complete record of their digital activities while maintaining their privacy.
Exploring the Potential of Blockchain Technology
Samsung Blockchain Keystore represents just the beginning of what’s possible with blockchain technology. As the technology continues to evolve, so too will its applications. From supply chain management to voting systems, blockchain technology has the potential to revolutionize a wide range of industries, offering enhanced security, transparency, and efficiency.
The Future of Digital Security
As we move forward into an increasingly digital world, the importance of digital security cannot be overstated. With solutions like Samsung Blockchain Keystore, users can rest assured that their digital assets are protected from unauthorized access and tampering. By leveraging blockchain technology, Samsung is paving the way for a more secure and transparent digital future.
Conclusion
Samsung Blockchain Keystore is more than just a digital security solution—it’s a glimpse into the future of digital transactions. With its advanced features and intuitive user interface, Samsung Blockchain Keystore empowers users to take control of their digital assets with confidence. As blockchain technology continues to evolve, Samsung remains at the forefront, leading the way towards a more secure and transparent digital future. Read more about samsung blockchain keystore