Unveiling Scott Stornetta: The Architect of Blockchain
The Genesis of Blockchain
Scott Stornetta stands as a towering figure in the world of technology, particularly renowned for his foundational work on blockchain. His journey into the realm of blockchain began in the early 1990s, long before the term gained mainstream recognition. Alongside Stuart Haber, Stornetta laid the groundwork for what would eventually become one of the most transformative technologies of the 21st century.
Pioneering the Concept
In a seminal paper published in 1991, Stornetta and Haber introduced the concept of a cryptographically secured chain of blocks, forming the basis of what we now know as blockchain. Their pioneering work addressed the challenge of tamper-proof digital timestamps, laying the foundation for the decentralized ledger system that underpins blockchain technology.
Revolutionizing Data Integrity
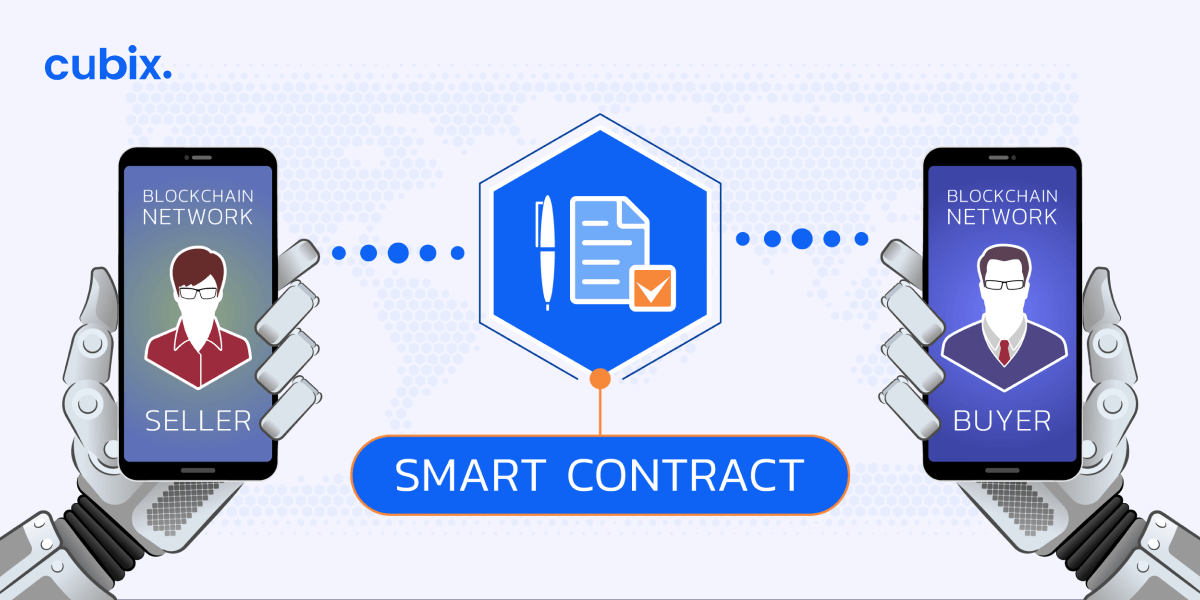
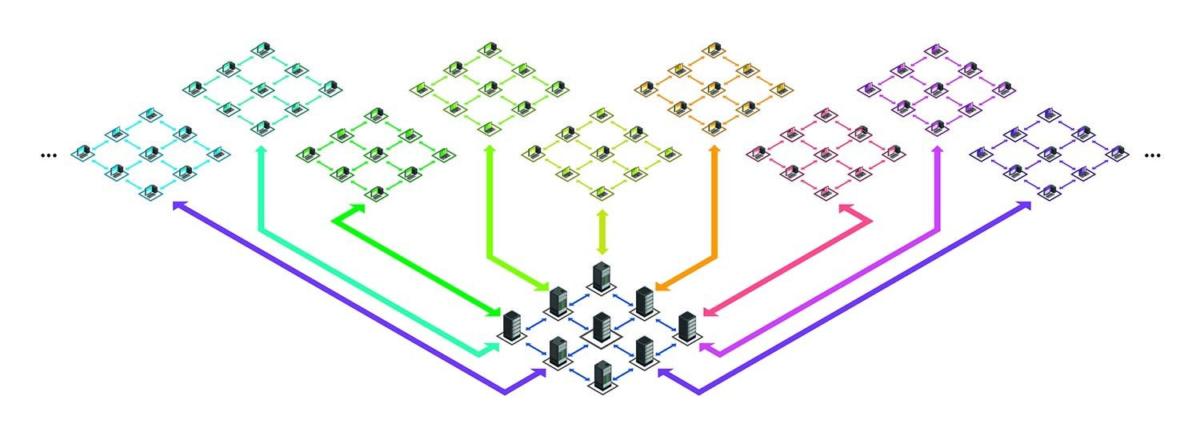
At its core, blockchain is a decentralized and immutable ledger that records transactions across a network of computers. Stornetta recognized early on the potential of blockchain to revolutionize data integrity, offering a secure and transparent way to record and verify transactions without the need for intermediaries.
Shaping the Future
Stornetta’s vision extended far beyond the realm of digital currencies. He foresaw blockchain’s potential to transform a wide range of industries, from finance to supply chain management to healthcare. By providing a tamper-proof record of transactions, blockchain has the power to enhance trust, accountability, and efficiency in countless applications.
Championing Transparency
One of the key benefits of blockchain technology is its ability to foster transparency and accountability. By providing a verifiable and immutable record of transactions, blockchain eliminates the need for trust in centralized authorities. This transparency has the potential to revolutionize industries plagued by fraud, corruption, and inefficiency.
Empowering Decentralization
Another hallmark of blockchain technology is its emphasis on decentralization. Unlike traditional centralized systems, which rely on a single point of control, blockchain distributes authority across a network of nodes. This decentralized structure not only enhances security but also promotes inclusivity and resilience.
Driving Innovation
As blockchain technology continues to evolve, Stornetta remains at the forefront of innovation. He continues to explore new applications and use cases for blockchain, pushing the boundaries of what is possible. From smart contracts to decentralized finance to non-fungible tokens (NFTs), blockchain has the potential to revolutionize virtually every aspect of our lives.
Overcoming Challenges
Of course, the road to widespread blockchain adoption has not been without its challenges. Scalability, interoperability, and regulatory concerns have all posed hurdles to blockchain’s mainstream adoption. However, Stornetta remains undeterred, confident in blockchain’s ability to overcome these obstacles and fulfill its promise as a transformative technology.
Looking Ahead
As we look to the future, one thing is clear: Scott Stornetta’s contributions to blockchain technology have laid the foundation for a new era of innovation and disruption. His visionary insights and pioneering spirit continue to inspire countless technologists, entrepreneurs, and visionaries around the world. With blockchain poised to reshape industries and redefine the way we interact with technology, the impact of Stornetta’s work will be felt for generations to come.