Renewable Energy Power Plant: Green Energy Hub
Harnessing Nature’s Resources
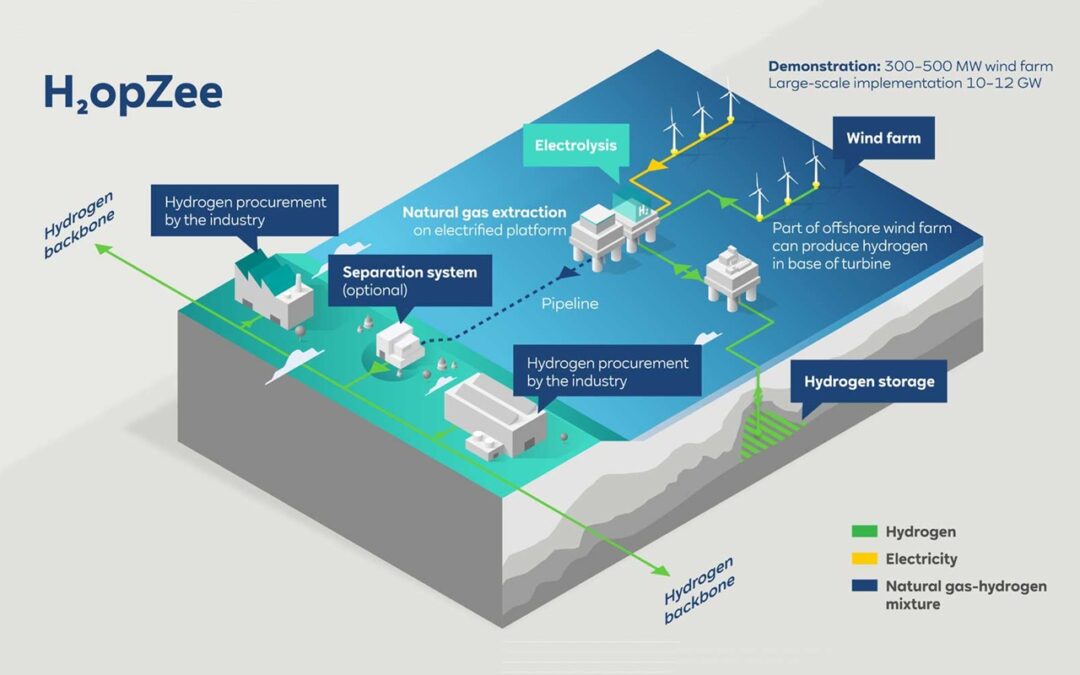
Renewable energy power plants serve as green energy hubs, harnessing the abundant and inexhaustible resources of nature to generate electricity. These power plants utilize renewable energy sources such as solar, wind, hydro, biomass, and geothermal energy to produce clean and sustainable electricity without depleting finite resources or emitting harmful pollutants. By tapping into the power of nature, renewable energy power plants play a crucial role in transitioning to a more sustainable and environmentally friendly energy system. To explore more about renewable energy power plants, visit here.
Solar Power Plants: Capturing Sunlight
Solar power plants harness the energy of the sun to generate electricity through photovoltaic panels or solar thermal systems. Photovoltaic panels convert sunlight directly into electricity using semiconductor materials, while solar thermal systems use mirrors or lenses to concentrate sunlight and generate heat for electricity production. Solar power plants can range from small-scale rooftop installations to utility-scale solar farms covering vast expanses of land, providing a reliable and abundant source of clean energy.
Wind Farms: Tapping into Wind Energy
Wind farms are another common type of renewable energy power plant, utilizing the kinetic energy of the wind to generate electricity through wind turbines. These turbines consist of large blades mounted on tall towers, which capture the wind’s energy and convert it into rotational motion to drive generators. Wind farms can be located onshore or offshore, depending on wind availability and site conditions, and can vary in size from small community-scale installations to large utility-scale projects supplying electricity to the grid.
Hydropower Plants: Harnessing Water Power
Hydropower plants harness the energy of flowing water to generate electricity through turbines and generators. These plants can utilize various water sources, including rivers, streams, and reservoirs, and can be classified into conventional hydropower plants, which rely on dams and reservoirs, and run-of-river hydropower plants, which divert a portion of the river’s flow through turbines without the need for large-scale dams. Hydropower plants provide a reliable and flexible source of renewable energy, contributing significantly to global electricity generation.
Biomass Power Plants: Utilizing Organic Materials
Biomass power plants convert organic materials such as wood, agricultural residues, and municipal solid waste into electricity through combustion or biochemical processes. These plants can use various feedstocks and technologies, including direct combustion, gasification, and anaerobic digestion, to produce heat and electricity with minimal environmental impact. Biomass power plants help reduce greenhouse gas emissions, promote waste management, and support rural economies by utilizing locally available biomass resources.
Geothermal Power Plants: Tapping Earth’s Heat
Geothermal power plants utilize the heat stored beneath the Earth’s surface to generate electricity through steam turbines and generators. These plants extract hot water or steam from geothermal reservoirs and use it to drive turbines, producing electricity with minimal emissions and environmental impact. Geothermal power plants can be located in areas with high geothermal activity, such as volcanic regions or geothermal hotspots, and provide a reliable and continuous source of renewable energy.
Advancing Renewable Technologies
Advancements