Exploring the Future of Finance with RBC Crypto
Understanding RBC Crypto
In the dynamic landscape of digital finance, RBC Crypto has emerged as a prominent player, offering a glimpse into the future of transactions. But what exactly is RBC Crypto, and how does it differ from traditional financial systems? Let’s delve into the intricacies of this innovative technology.
The Evolution of Transactions
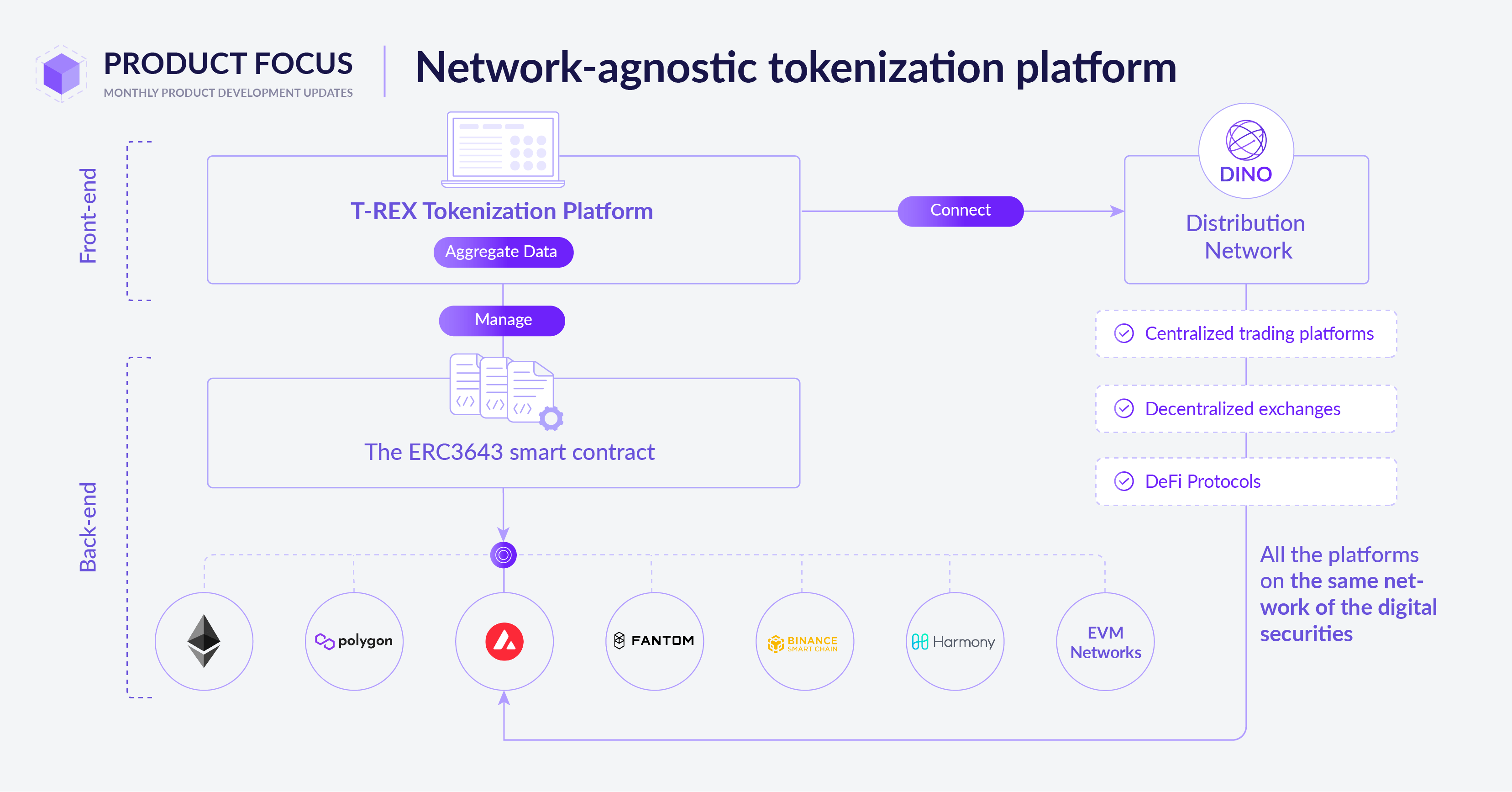
Traditional financial systems rely heavily on intermediaries such as banks and payment processors to facilitate transactions. However, RBC Crypto seeks to disrupt this model by leveraging blockchain technology to enable peer-to-peer transactions. This decentralized approach eliminates the need for intermediaries, resulting in faster, more efficient, and cost-effective transactions.
Security and Transparency
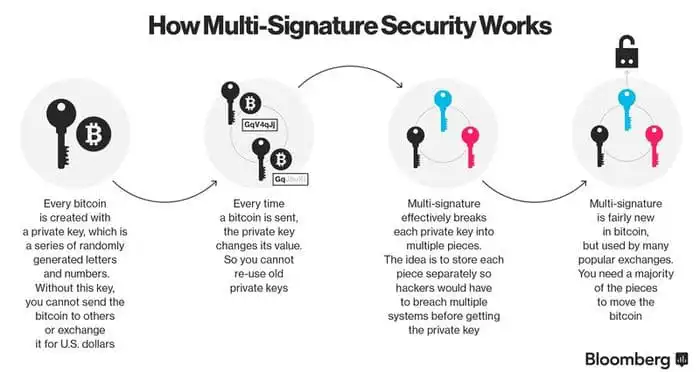
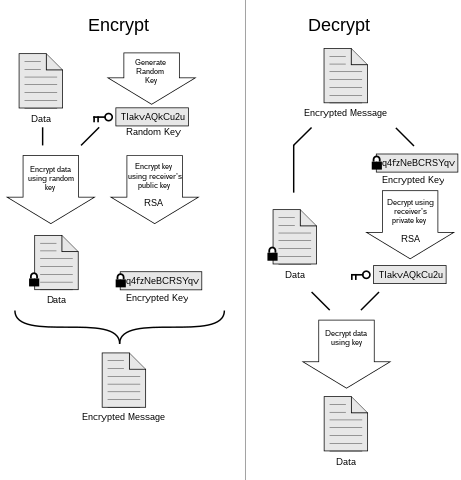
One of the key advantages of RBC Crypto is its emphasis on security and transparency. Unlike traditional financial systems, where transactions can be susceptible to fraud and manipulation, RBC Crypto uses cryptographic techniques to ensure the integrity and security of transactions. Additionally, the transparent nature of the blockchain allows for real-time visibility into transaction histories, promoting trust and accountability.
Empowering Financial Inclusion
Financial inclusion is a pressing issue globally, with millions of people lacking access to basic banking services. RBC Crypto has the potential to address this challenge by providing a decentralized platform for financial transactions. By enabling individuals to participate in the global economy without the need for a traditional bank account, RBC Crypto can empower underserved populations and drive economic growth.
Innovating Financial Systems
RBC Crypto is not just a technological innovation; it’s a catalyst for change in the way financial systems operate. Its decentralized nature reduces reliance on centralized authorities, making transactions more resilient to censorship and manipulation. Additionally, the use of smart contracts allows for the automation of complex financial processes, further streamlining operations.
Challenges and Opportunities
While RBC Crypto holds immense promise, it also faces significant challenges. Regulatory uncertainty, scalability issues, and concerns about energy consumption are just a few of the hurdles that must be overcome for widespread adoption. However, with the right approach and collaboration, these challenges can be addressed, unlocking the full potential of RBC Crypto to revolutionize the financial industry.
Adoption and Integration
The success of RBC Crypto ultimately hinges on its adoption and integration into existing financial systems. While some institutions may be hesitant to embrace this disruptive technology, others are already exploring ways to incorporate blockchain into their operations. As more organizations recognize the benefits of RBC Crypto, we can expect to see increased adoption and integration across various sectors.
The Future of Finance
In conclusion, RBC Crypto represents a paradigm shift in the way we think about finance. By leveraging blockchain technology, it offers a decentralized alternative to traditional financial systems, empowering individuals and organizations to transact securely and efficiently. While challenges remain, the potential of RBC Crypto to revolutionize the financial industry is undeniable, paving the way for a more inclusive, transparent, and resilient future of finance. Read more about rbc crypto