Understanding Merkle Trees in Blockchain: Enhancing Data Integrity Blockchain technology has revolutionized the way we handle data, introducing new concepts…
Read More

Understanding Merkle Trees in Blockchain: Enhancing Data Integrity Blockchain technology has revolutionized the way we handle data, introducing new concepts…
Read More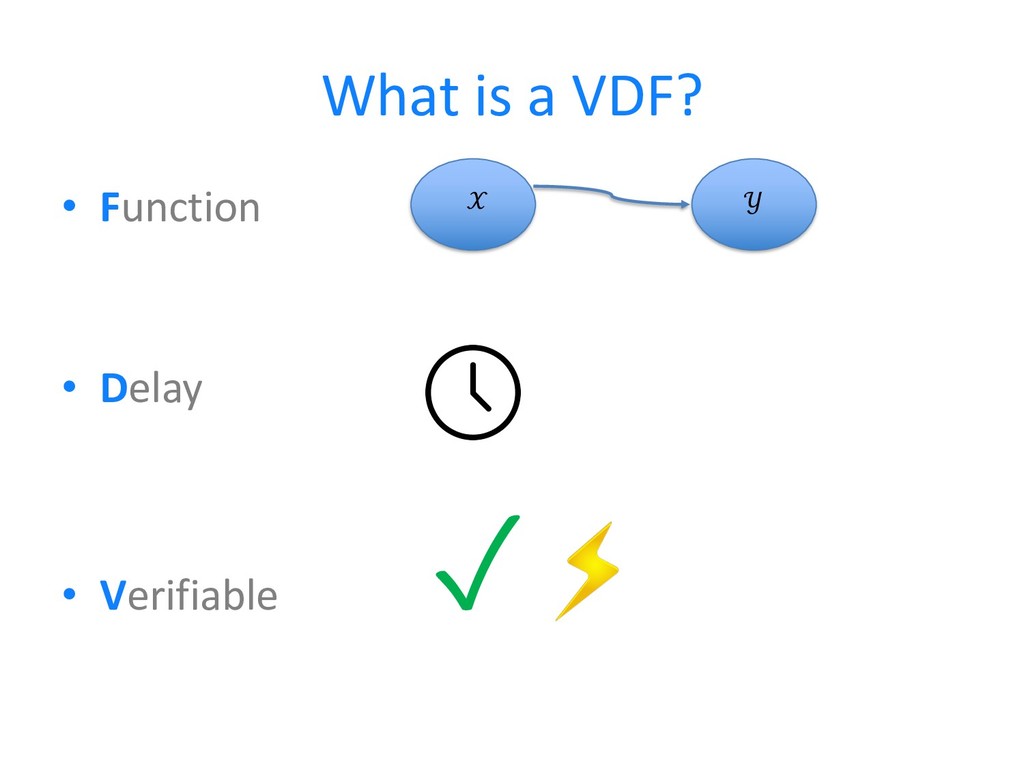
Unraveling Cryptographic Verifiable Delay Functions (VDFs) Cryptographic Verifiable Delay Functions (VDFs) are an intriguing facet of modern cryptography, serving as…
Read More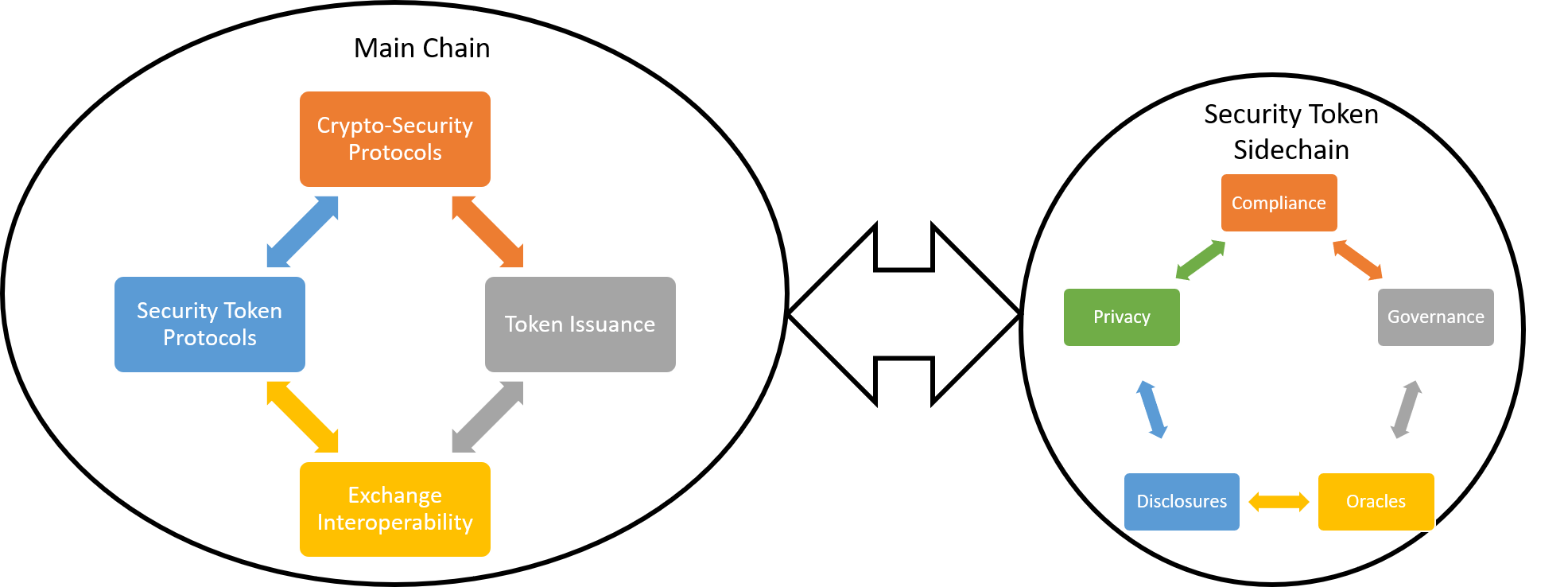
Securing Transactions: Exploring Sidechain Security Measures Sidechains have emerged as a versatile solution to scalability issues in blockchain networks. This…
Read MoreUnraveling the Path of Evolution: Understanding Forks in Blockchain Blockchain technology, the backbone of cryptocurrencies and decentralized applications, experiences a…
Read More
Exploring Byzantine Fault Tolerance: Navigating Reliability in Blockchain In the intricate landscape of blockchain technology, Byzantine Fault Tolerance (BFT) stands…
Read More
Interwoven Chains: Safeguarding Transactions with Cross-Chain Security Cross-chain security has become a pivotal consideration in the ever-expanding blockchain landscape. In…
Read More
Decoding the Intricacies of Blockchain Mining Blockchain technology has undoubtedly been a revolutionary force, transforming industries and reshaping how we…
Read More
The Importance of Secure Random Number Generation Secure random number generation is a critical component in the realm of cybersecurity,…
Read More
Securing Data Integrity on the Blockchain: A Definitive Approach Blockchain technology has emerged as a robust solution for securing data…
Read More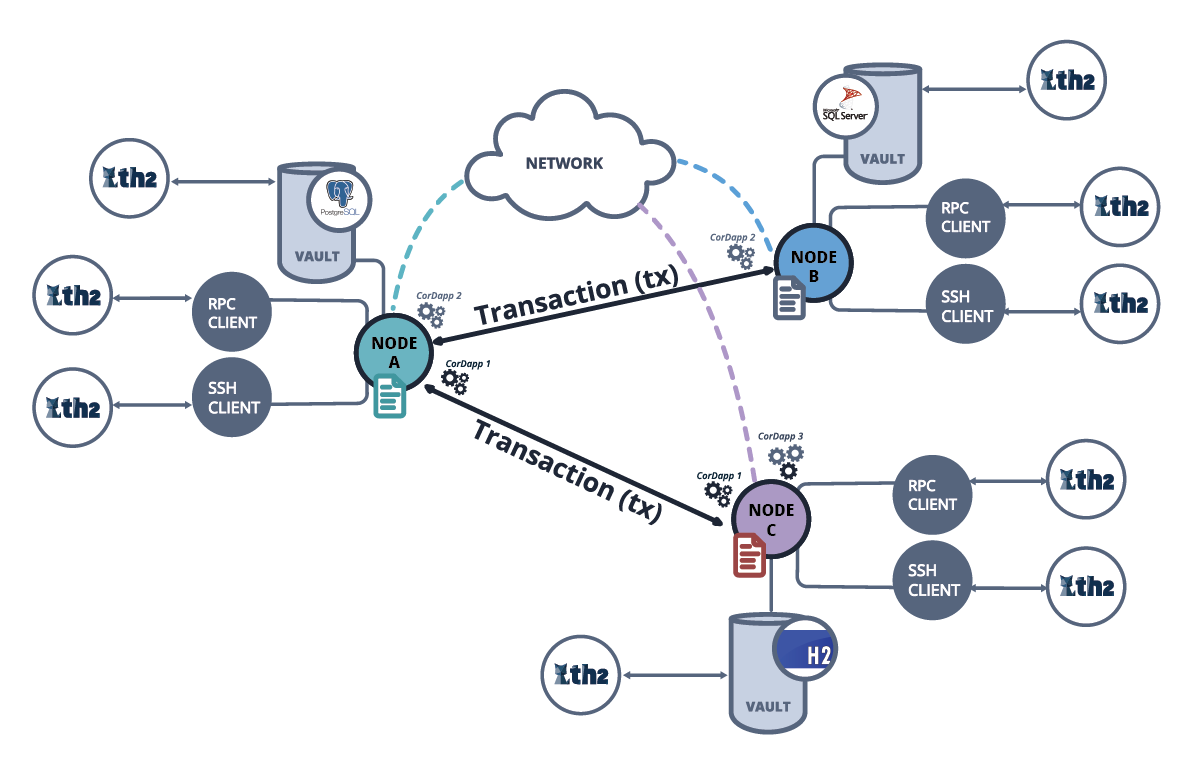
Transforming Records: A Dive into Distributed Ledger Technology Exploring the realm of Distributed Ledger Technology (DLT) reveals a paradigm shift…
Read More
In the ever-evolving landscape of technology, the concept of decentralization has gained significant prominence. From finance to governance, decentralized systems…
Read More
Forging Unity: Navigating Blockchain Consensus Blockchain consensus mechanisms form the bedrock of decentralized systems, ensuring agreement on transaction validity. This…
Read More
Blockchain Confidentiality: Safeguarding Data in the Digital Ledger Blockchain technology, known for its transparency, also provides robust solutions for data…
Read More