Introduction: In the bustling world of smartphones, Apple’s latest unveiling, the iPhone SE 2020 64GB, has captured the attention of…
Read More

Introduction: In the bustling world of smartphones, Apple’s latest unveiling, the iPhone SE 2020 64GB, has captured the attention of…
Read More
Shiloh Jolie Pitt: TikTok Sensation in the Making A Glimpse into Shiloh’s World Shiloh Jolie Pitt, the daughter of Hollywood…
Read More
Unlocking the Power of Snap TikTok MP3 Exploring Snap TikTok MP3 Snap TikTok MP3 has become a game-changer in the…
Read More
The Next Generation Samsung Galaxy A03 Features Revealed Affordable Innovation: A Game-Changer in the Smartphone Market Samsung has long been…
Read More
Shibarium Blockchain: Redefining Decentralized Finance Introduction: The Rise of Shibarium Blockchain In the ever-evolving landscape of blockchain technology, Shibarium has…
Read More
Unraveling the Economics: Analyzing Hydrogen Production Plant Cost Understanding the Investment Landscape Hydrogen production plants are emerging as pivotal players…
Read More
Best Renewable Energy Source: Powering the Future Renewable energy sources are increasingly gaining prominence as the world seeks sustainable alternatives…
Read More
Revolutionizing the Energy Landscape: Exploring Renewable Energy Inventions Innovating for Sustainability Renewable energy inventions have sparked a revolution in the…
Read More
Exploring Sustainable Solutions: Renewable Energy Products for Homes Embracing Renewable Energy In today’s world, the shift towards sustainability and renewable…
Read More
In the realm of renewable energy, the spotlight often shines on sources like solar and wind power. However, one critical…
Read MoreEco-Friendly Technology: Innovating for a Sustainable Future In today’s era of heightened environmental awareness, eco-friendly technology has emerged as a…
Read More
Driving Clean Energy Innovation: Electrolyzer Green Hydrogen A Breakthrough in Sustainable Energy Electrolyzer green hydrogen represents a groundbreaking advancement in…
Read More
Green Hydrogen: Revolutionizing Storage & Transportation In the realm of sustainable energy, green hydrogen has emerged as a game-changer, offering…
Read More
Tokenization: Transforming Assets into Digital Value The concept of tokenization is revolutionizing the way we perceive and handle various forms…
Read MoreUnlocking Privacy: The Power of Secure Multi-Party Computation In the realm of digital privacy and secure data collaboration, Secure Multi-Party…
Read More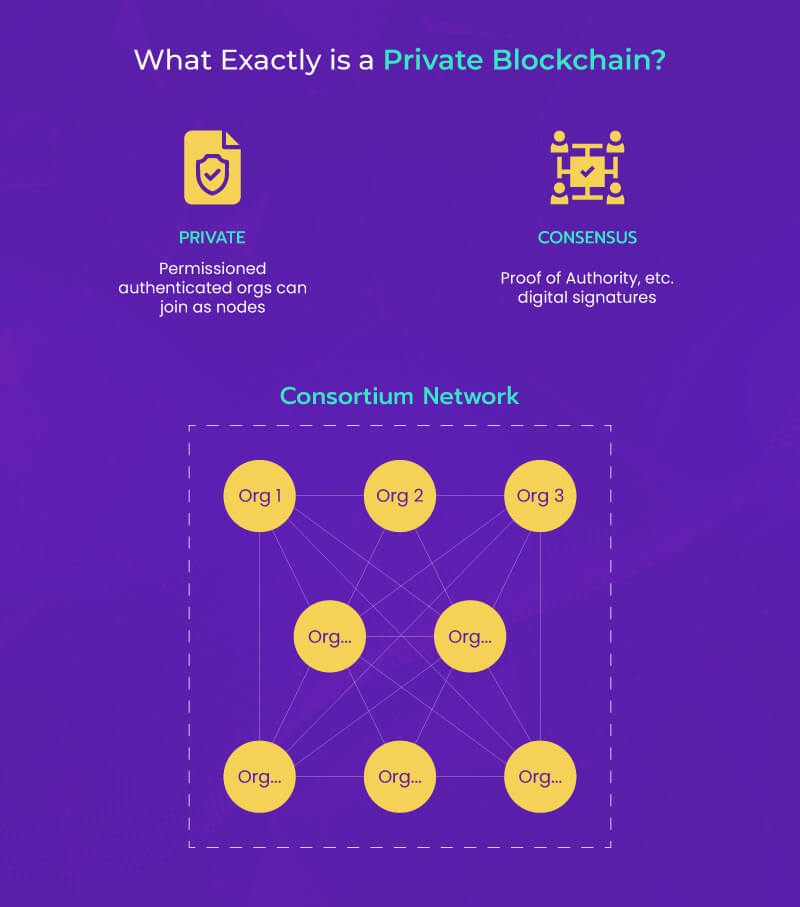
Securing Transactions: Private Blockchain Network Essentials Blockchain technology, initially popularized by public cryptocurrencies, has evolved to cater to various business…
Read More
TraceGuard: Ensuring Secure Supply Chain Provenance In an era where supply chain transparency is paramount, the integration of blockchain technology…
Read More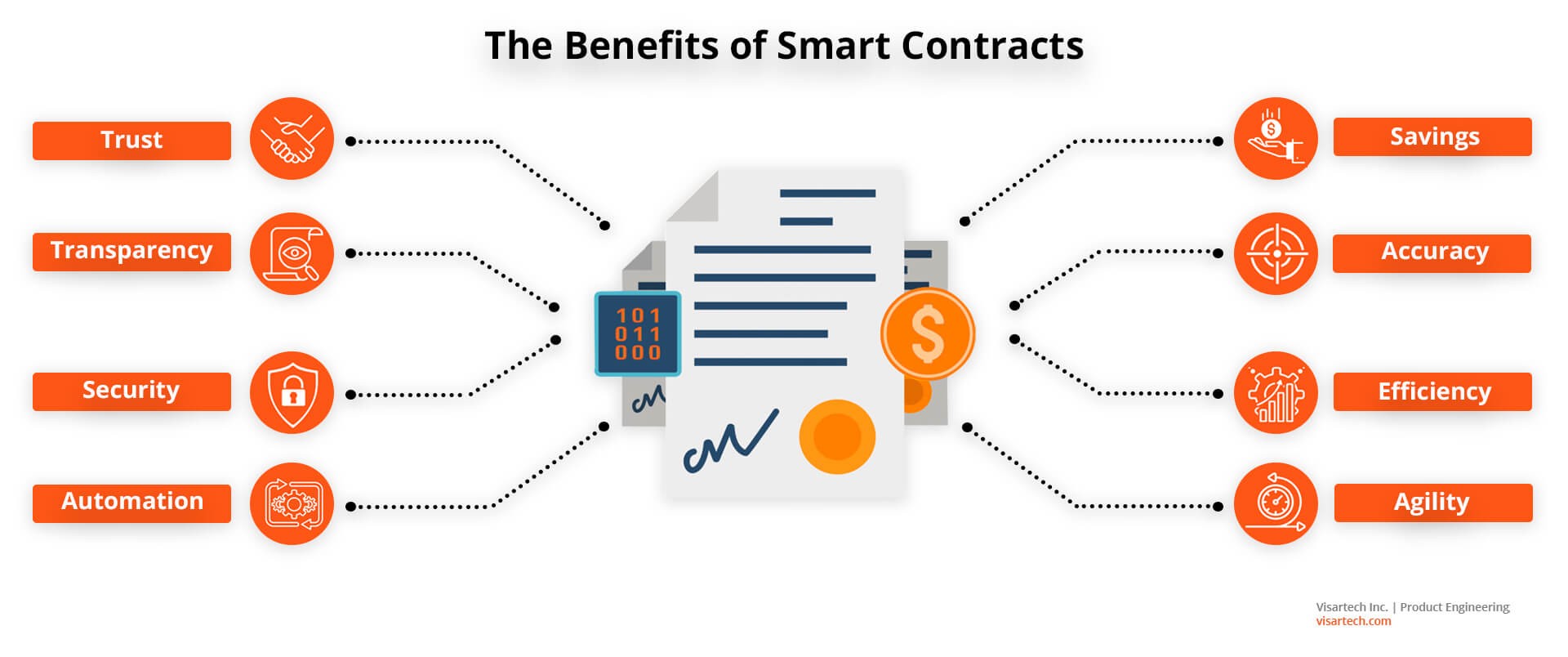
Revolutionizing the Music Industry: The Security of Tokenized Music Contracts In the ever-evolving landscape of the music industry, the introduction…
Read More
Ensuring Resilience: Navigating Through Comprehensive Security Audits Security audits play a pivotal role in safeguarding digital assets and fortifying systems…
Read More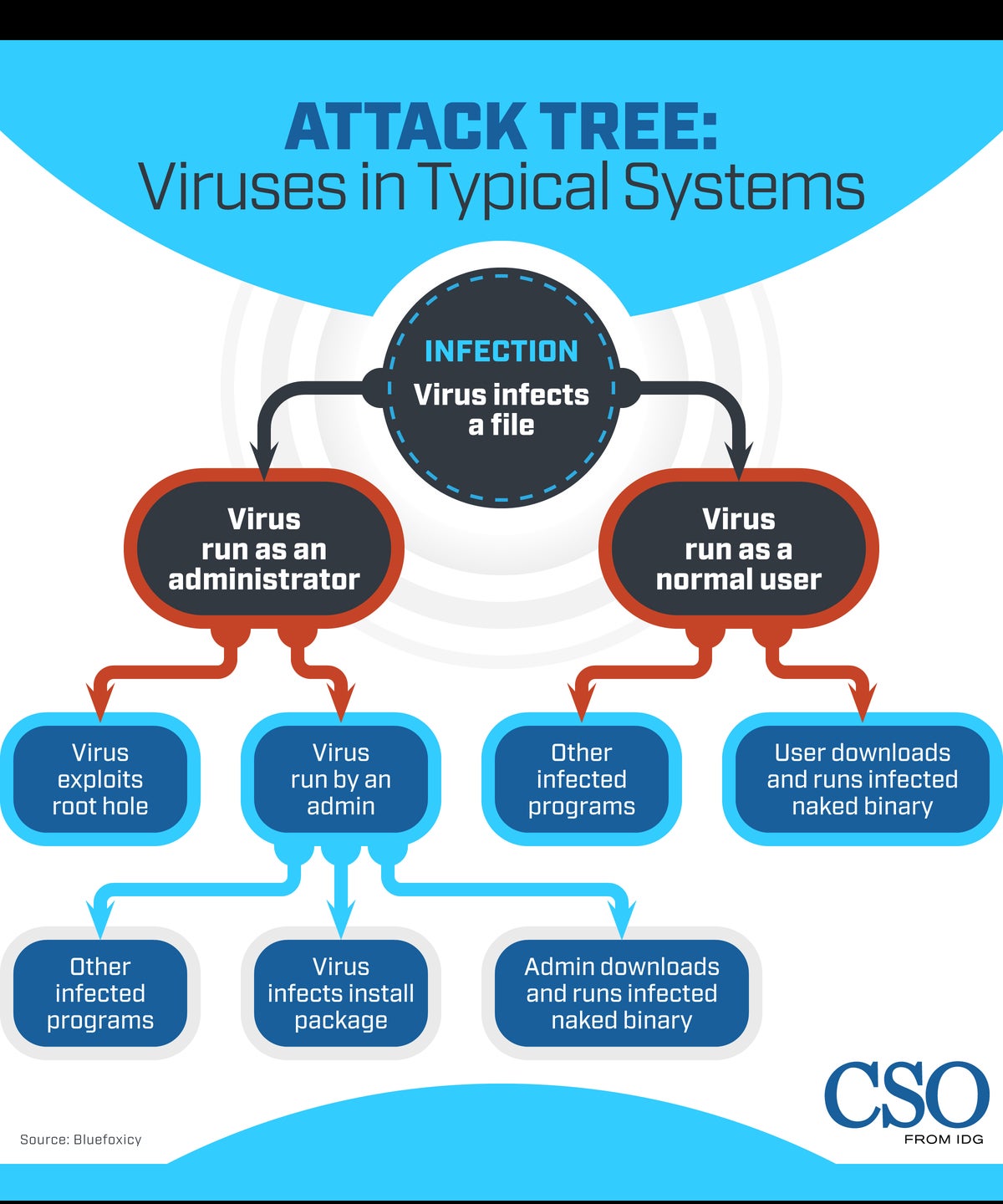
Decoding Risks: Navigating Blockchain Security with Threat Modeling Blockchain technology, celebrated for its decentralized and secure nature, is not exempt…
Read More