B2B SaaS sales, or Business-to-Business Software as a Service sales, is a dynamic and evolving field that involves selling cloud-based…
Read More

B2B SaaS sales, or Business-to-Business Software as a Service sales, is a dynamic and evolving field that involves selling cloud-based…
Read More
A Chic Introduction: Setting the Scene The iPhone 13 Mini in its elegant pink hue is more than just a…
Read More
Introduction: The Galaxy Note 10 Lite is making waves in the smartphone world, promising power and performance at an accessible…
Read More
Introduction: In a world dominated by smartphones the size of small tablets, there’s a growing demand for something more compact,…
Read More
Introducing the Apple Watch SE 2021 The Ultimate Fitness Partner In today’s fast-paced world, staying fit and healthy is more…
Read More
Subheading: Introducing the Samsung Galaxy A02s In the ever-evolving landscape of smartphones, Samsung has once again raised the bar with…
Read More
Exploring the Shaka Boom Phenomenon on TikTok Unveiling the Shaka Boom: TikTok’s Latest Sensation In the ever-evolving landscape of social…
Read More
Introduction: Unleashing the Power of Samsung’s 45W Charger In the ever-evolving landscape of technology, one constant desire remains: the need…
Read More
Introduction: In the fast-paced world of smartphones, OnePlus has long been known for delivering high-quality devices at competitive prices. With…
Read More
Unlocking the Potential of Secret Network Crypto Understanding Secret Network Crypto Secret Network Crypto, often referred to simply as Secret…
Read More
Introduction: In today’s fast-paced world, music has become an integral part of our daily lives. Whether we’re commuting to work,…
Read More
Exploring the Legacy of Rodger Cleye Introduction: The Visionary Leader Rodger Cleye, a name synonymous with innovation and success, has…
Read More
Deciphering the Trend: Salty Ice Cream TikTok Meaning Understanding the Phenomenon Salty Ice Cream TikTok has taken social media by…
Read More
Exploring TikTok’s Salty Ice Cream Craze The Rise of TikTok Trends In the vast world of social media, TikTok stands…
Read More
Unleash the Fun: Shaka Boom TikTok Trends Explained The Rise of Shaka Boom In the ever-evolving landscape of TikTok trends,…
Read More
Sub Heading: The Rise of Innovative Renewable Energy Technology in 2022 The quest for sustainable energy solutions has gained significant…
Read More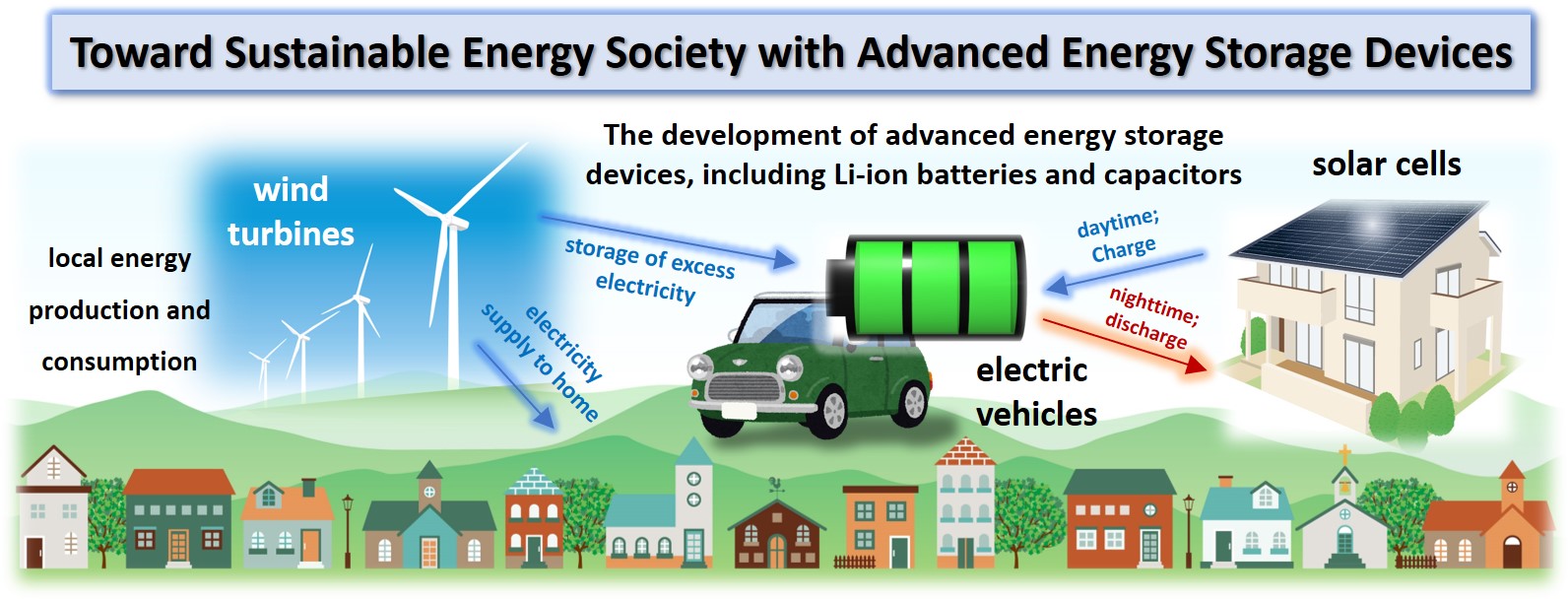
Innovating for the Future: Sustainable Energy Storage Solutions The Importance of Sustainable Energy Storage Sustainable energy storage is increasingly recognized…
Read More
Green Tech Innovations: Sustainable Solutions Driving Environmental Progress In the realm of sustainability, green tech solutions are driving significant progress…
Read More
Sustainable Solutions: Integrating Renewable Energy in Architecture In the realm of architecture, the integration of renewable energy solutions is becoming…
Read More
Unleashing the Potential of Sustainable Renewable Energy Harnessing Nature’s Bounty Sustainable renewable energy represents the pinnacle of human ingenuity, as…
Read More
Understanding Merkle Trees in Blockchain: Enhancing Data Integrity Blockchain technology has revolutionized the way we handle data, introducing new concepts…
Read More
Exploring the Cutting Edge: Renewable Energy Innovation Pioneering New Technologies Renewable energy innovation is at the forefront of shaping tomorrow’s…
Read More
Transformative Decentralized Applications Platform: Exploring Ethereum In the realm of blockchain technology, Ethereum stands out as a transformative platform that…
Read MoreSecuring Consensus Participants for Robust Blockchain Systems Blockchain systems rely on a decentralized consensus mechanism to validate and agree upon…
Read More
Navigating Cyber Storms: Strategies for Resilience Against DDoS Attacks Distributed Denial-of-Service (DDoS) attacks continue to pose a significant threat to…
Read More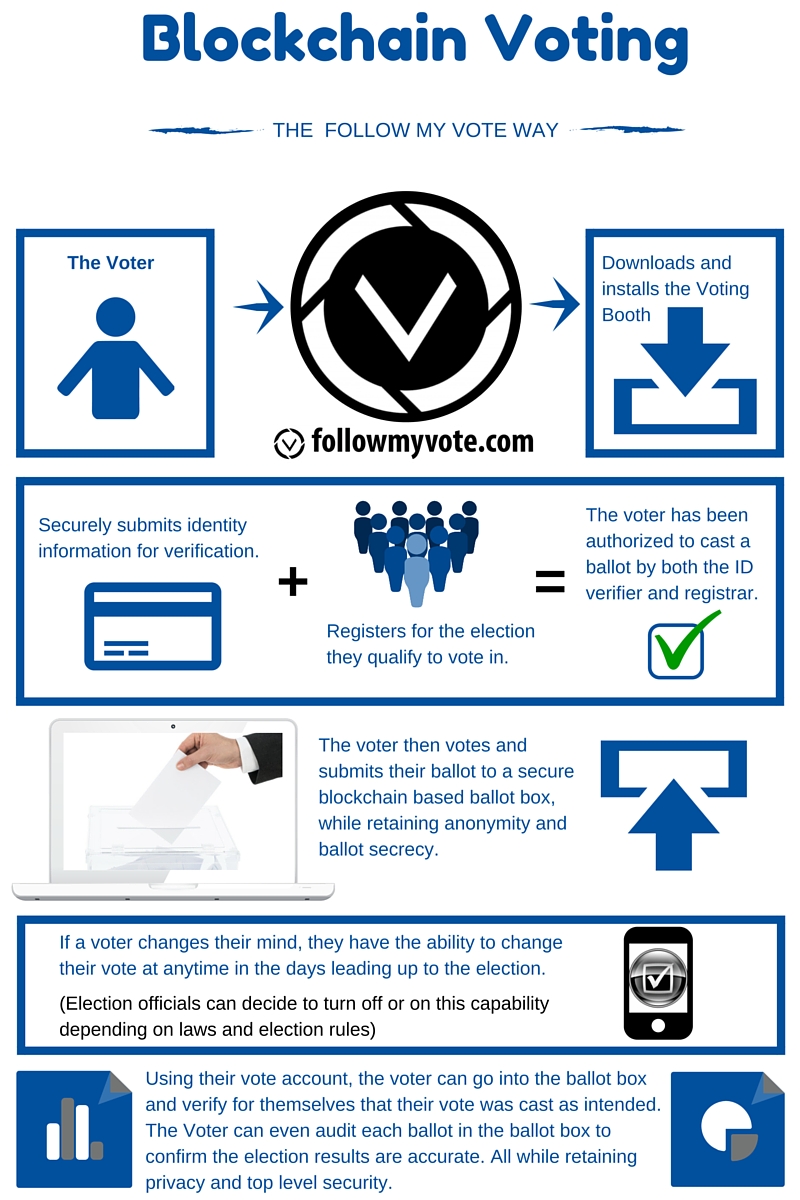
Advancing Electoral Integrity with Secure Blockchain Voting Blockchain technology is increasingly being explored as a solution to enhance the security…
Read More
DeFi Security: Safeguarding the Decentralized Financial Landscape Decentralized Finance (DeFi) has garnered immense popularity for its innovative approach to financial…
Read More
Ensuring Security: Token Standards like ERC-20, ERC-721 Token standards, such as ERC-20 and ERC-721, have become integral components of blockchain…
Read More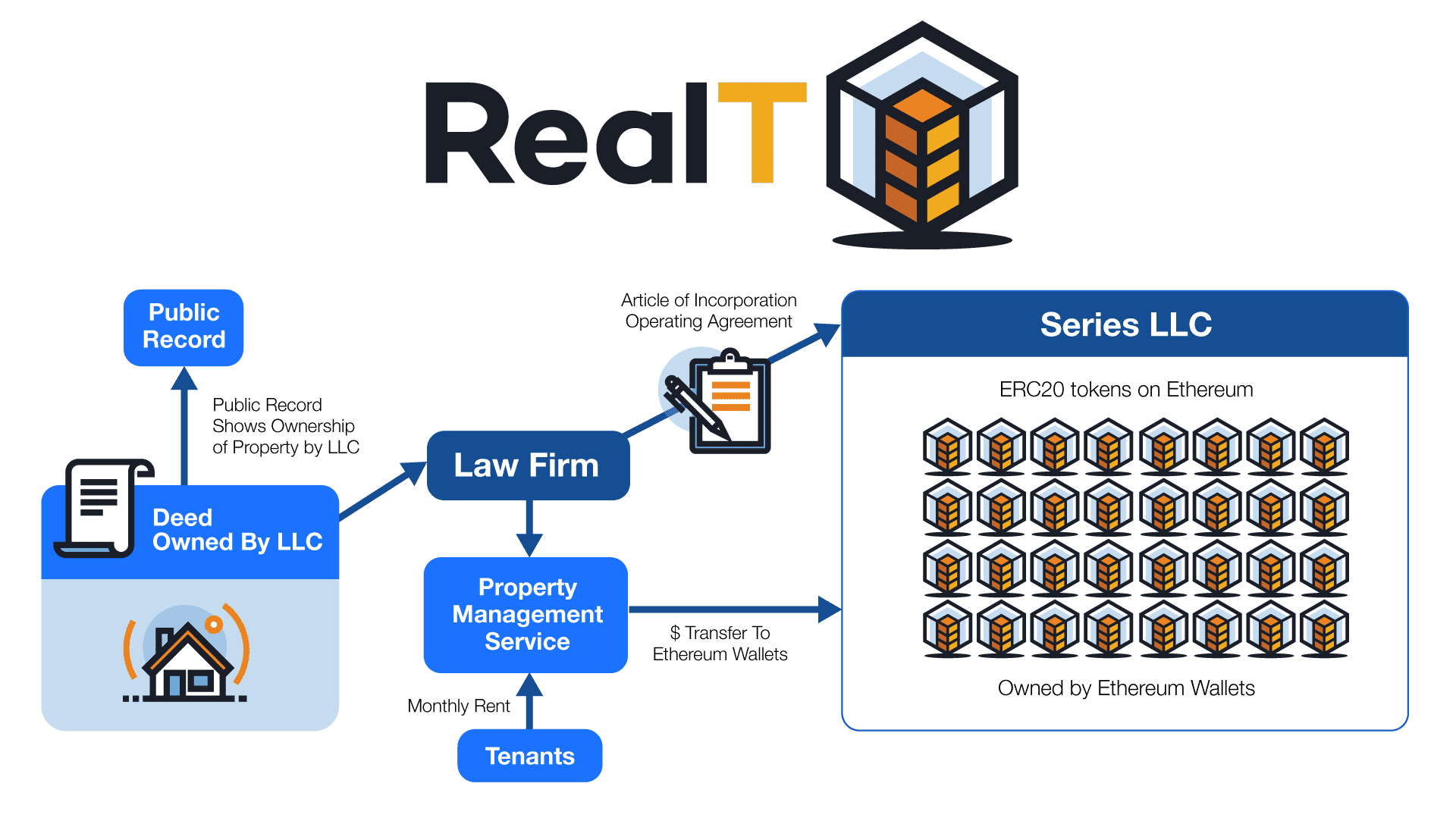
Revolutionizing Innovation: The Security of Tokenized Intellectual Property In the ever-evolving landscape of intellectual property (IP) management, the concept of…
Read More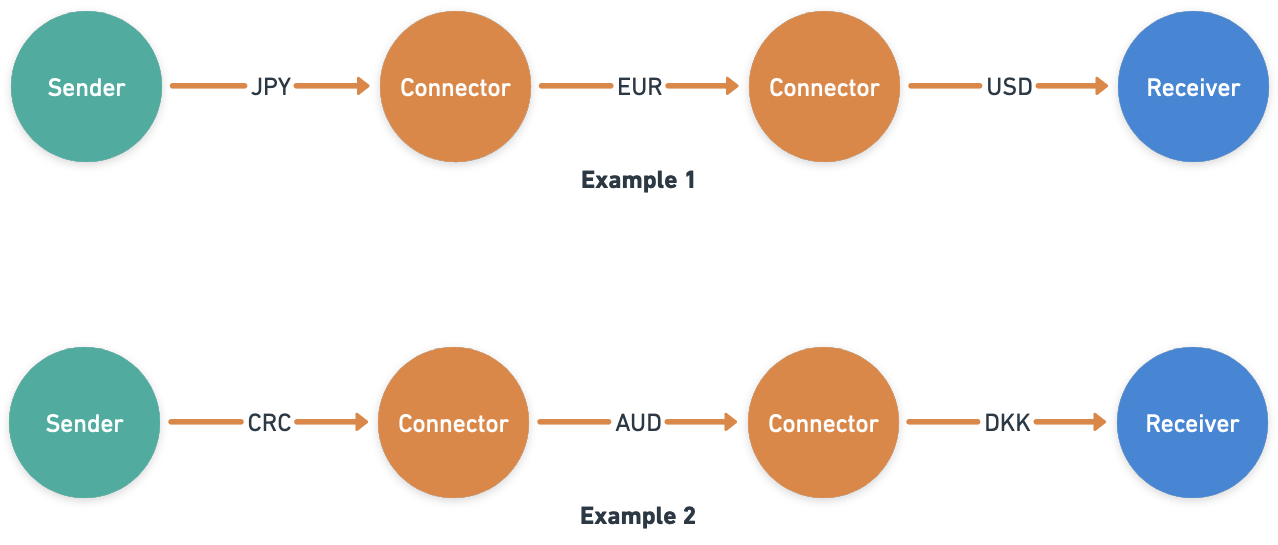
Interledger Protocols: Bridging Digital Transactions Interledger protocols have revolutionized the landscape of digital transactions, providing a seamless bridge between various…
Read More
Revolutionizing the Art World: The Security of Tokenized Art Contracts In the vibrant realm of the art market, the advent…
Read More
CryptoVault: Elevating Data Storage Security with Blockchain In the digital age, the security of data storage is paramount, and the…
Read More
Software Wallets: Flexible Solutions for Digital Asset Management The world of digital assets offers various storage solutions, and software wallets…
Read More
Interconnected Chains: Navigating Federated Blockchain Solutions Federated blockchains, also known as federated or consortium blockchains, represent a collaborative approach to…
Read More
Blockchain Chain Analysis: Uncovering Digital Transactions Blockchain technology has revolutionized the way transactions are conducted, bringing transparency and security to…
Read More
Fortifying Transactions: The Power of Secure Tokenized Service Agreements In a digitally-driven business landscape, the demand for secure and efficient…
Read MoreWhether it’s Android or iOS, we need to know how to get good video results. This is because it will…
Read MoreAre you annoyed if your phone memory is often full? Yeah, this is very unpleasant because it makes the mobile…
Read MoreFamiliarize yourself with handy tips and trick is necessary especially for newbies. It because can be speed up the activities…
Read MoreThere are several problems that can cause problems with your iPhone storage. This could be due to too many applications…
Read MoreHaving smartphone can be easier for us to do some activities. We can do any online activities such as shopping,…
Read MoreThe development of gadgets makes people addicted to smartphones. We can see that people are always on their smartphones everywhere…
Read More