Navigating the Digital Landscape The digital world is constantly evolving, and businesses need to adapt to stay competitive. This means…
Read More

Navigating the Digital Landscape The digital world is constantly evolving, and businesses need to adapt to stay competitive. This means…
Read More
Subheading: Introducing the Google Pixel 6a In a world where smartphones are an extension of ourselves, the Google Pixel 6a…
Read More
Key Takeaways Land management incorporates diverse techniques to optimize both productivity and sustainability. Technological advancements and sustainable practices are paramount…
Read More
Introduction: In the ever-evolving landscape of mobile technology, Samsung has continually pushed the boundaries of innovation. With each new release,…
Read More
Introduction: In a world where technology constantly evolves, connectivity is key. And Samsung understands this better than anyone. Enter the…
Read More
Introduction: In today’s fast-paced world, convenience is key, especially when it comes to purchasing the latest gadgets like iPhones. Luckily,…
Read More
Unveiling the Wonders of Sensorium Galaxy A New Frontier in Digital Entertainment Sensorium Galaxy has emerged as a beacon of…
Read More
Unveiling the Story of Sejarah Metaverse A Journey Through Digital Realms The concept of Sejarah Metaverse has captured the imagination…
Read More
Dive into the Colorful World of Slime Storytime Unlocking Creativity: The Magic of Slime In the realm of storytelling, few…
Read More
Exploring Samsung 837X: A Tech Enthusiast’s Haven Revolutionizing Tech Experience Samsung 837X stands as a beacon of innovation, redefining the…
Read More
Read more about qualcomm metaverse…
Read More
Sienna Mae TikTok: Unveiling Creative Brilliance Introducing Sienna Mae TikTok: A Platform of Artistic Expression Sienna Mae TikTok has emerged…
Read More
Exploring Samsung’s Metaverse: A Digital Revolution Unveiling the Virtual Frontier In the ever-evolving landscape of technology, Samsung has once again…
Read More
Exploring the Digital Wonderland of Skt Ifland The Allure of Virtual Realms In today’s fast-paced digital age, virtual reality (VR)…
Read More
The Rise of Queen Cheryl: TikTok’s Reigning Monarch Unveiling the TikTok Sensation In the realm of social media, few figures…
Read More
Renewable energy has emerged as a cornerstone of sustainable development, offering a diverse array of options to power our world…
Read More
Eco-Friendly Technology Examples: Shaping a Sustainable Future Innovative Solar Power Solutions Solar power stands as a beacon of eco-friendly technology,…
Read More
Driving Sustainability Forward with Advanced Green Technologies In the age of climate change and environmental concerns, the emergence of advanced…
Read More
Green Hydrogen Fuel Cell: Clean Power Solution Understanding Green Hydrogen Green hydrogen fuel cell technology represents a promising avenue for…
Read More
Pioneering Sustainable Solutions Through Green Technology Innovation The Rise of Green Technology In recent years, there has been a significant…
Read More
Longi Green Energy Technology Co Ltd LR4 60HPH 365M: Solar Innovation Revolutionizing Solar Technology Longi Green Energy Technology Co Ltd…
Read More
Pioneering Sustainable Solutions: Green Energy Storage Systems The Quest for Sustainable Energy Storage In the pursuit of a greener future,…
Read More
Exploring Green Education: Renewable Energy Schools Nearby Embracing a Sustainable Future Renewable energy schools nearby offer a unique opportunity to…
Read More
Hydrogen has emerged as a promising contender in the quest for sustainable energy solutions, offering a clean and versatile fuel…
Read More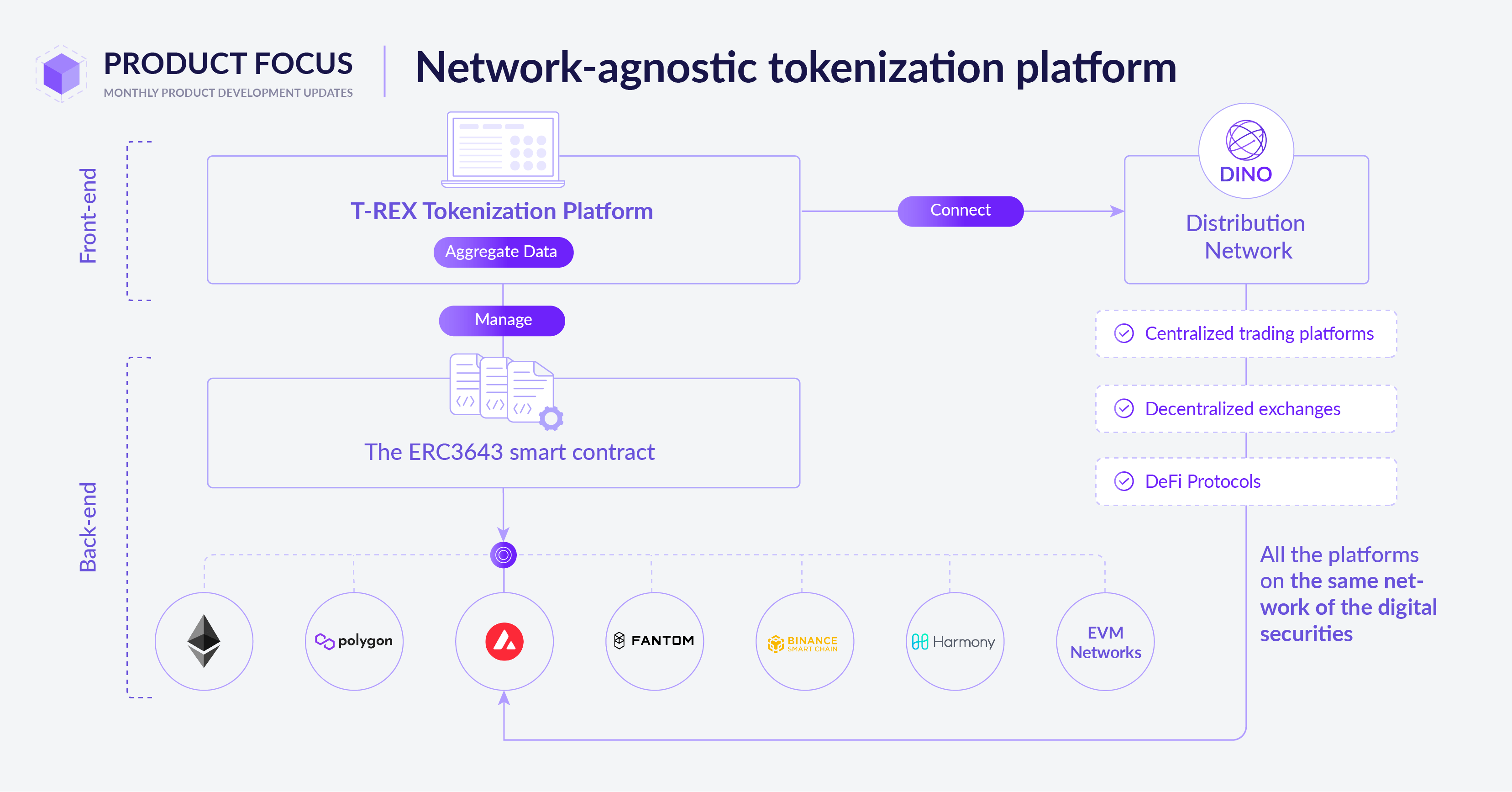
Understanding Security Tokenization Security tokenization is a powerful strategy in the realm of cybersecurity, offering enhanced protection for sensitive data.…
Read More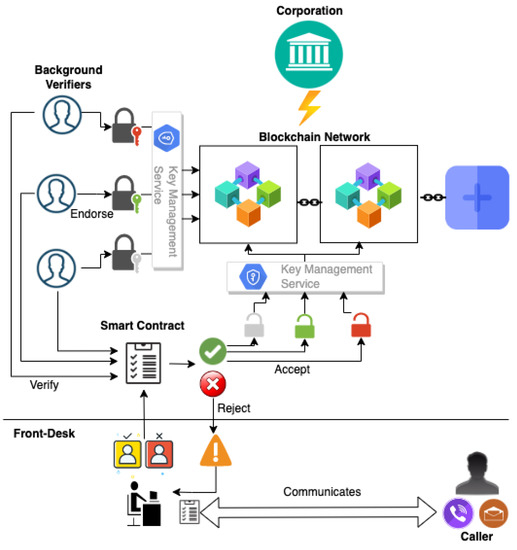
Understanding and Mitigating Blockchain Attacks: Strategies and Insights Blockchain technology, hailed for its security and transparency, is not immune to…
Read More
Best Hydrogen Electrolyzer: Cutting-Edge Technology Unveiling the Pinnacle of Hydrogen Production In the realm of hydrogen production, the search for…
Read More
Securing DApps: Enhancing Trust in Decentralized Applications Decentralized applications (DApps) operate on blockchain networks, offering users the benefits of transparency,…
Read More
Navigating the Landscape: Blockchain Interoperability Standards The blockchain ecosystem, with its decentralized and distributed nature, has revolutionized various industries. However,…
Read More
Exploring the World of Secure Liquidity Pools in DeFi Decentralized Finance (DeFi) has reshaped the financial landscape, offering innovative ways…
Read More
Securing Data Integrity on the Blockchain: A Definitive Approach Blockchain technology has emerged as a robust solution for securing data…
Read More
Maximizing Hash Rate: Strategies for Optimal Cryptocurrency Mining In the world of cryptocurrency mining, achieving a high hash rate is…
Read More
Secure Transactions: Privacy-Focused Blockchain Solutions Privacy-focused blockchains have emerged as a solution to address the growing concerns regarding the confidentiality…
Read More
The Growing Trend of Token Swaps In the dynamic realm of blockchain and cryptocurrency, token swaps have become an integral…
Read More