Elevating Security: Future-Ready Tokenized Employment Contracts
In a rapidly digitizing world, the landscape of employment contracts is evolving. Secure tokenized employment contracts are emerging as a groundbreaking solution, not only enhancing security but also revolutionizing the way employment agreements are managed and executed.
Tokenization Reshaping Employment Contract Security
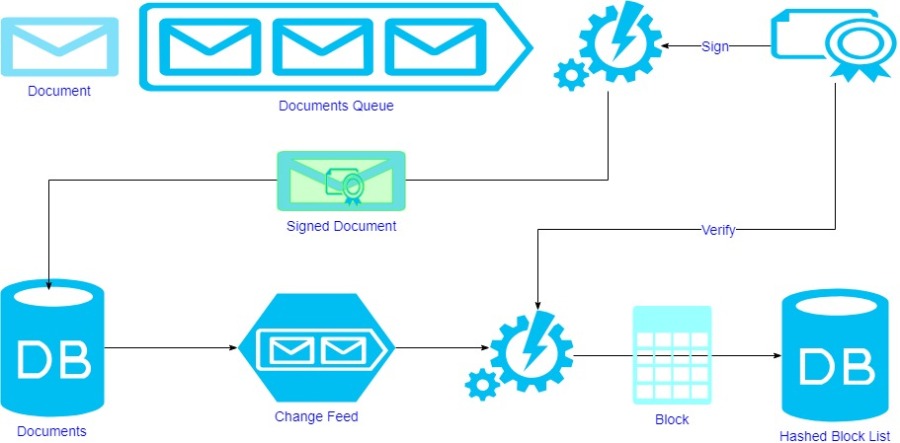
At the core of secure tokenized employment contracts is the innovative process of tokenization. By leveraging blockchain technology, these contracts transform traditional agreements into digital tokens. This not only bolsters security by preventing unauthorized modifications but also provides an immutable record on the blockchain, ensuring the integrity of employment terms.
Blockchain Security: Safeguarding Employment Transactions
The inherent security features of blockchain play a crucial role in the realm of secure tokenized employment contracts. The decentralized and tamper-resistant nature of blockchain ensures that employment data remains secure and transparent. This fortified security mitigates risks associated with fraud and unauthorized alterations to employment terms.
Smart Contracts: Revolutionizing Employment Agreement Execution
Embedded within secure tokenized employment contracts are smart contracts, self-executing programs that automate the enforcement of contract terms. This automation streamlines the execution of employment agreements, reducing the need for intermediaries and ensuring that contractual obligations are met efficiently and without delays.
Decentralization in Employment Contract Management
The adoption of secure tokenized employment contracts represents a shift towards decentralized employment contract management structures. Traditional employment contracts often involve intermediaries and multiple layers of bureaucracy. The decentralized approach empowers stakeholders by directly recording and governing employment terms on the blockchain, fostering transparency and efficiency.
Cryptographic Security: Enhancing Confidentiality in Employment Contracts
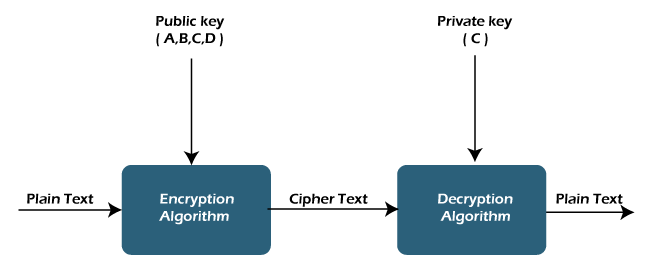
The application of cryptographic principles in secure tokenized employment contracts ensures the confidentiality of sensitive employment information. Each party involved is assigned unique cryptographic keys, establishing a secure channel for communication and data exchange. This cryptographic layer adds an extra dimension of privacy and protection to employment transactions.
Tokenization: Transforming Employment Asset Representation
Tokenization not only enhances security but also redefines how employment assets are represented. Digital tokens serve as unique, tamper-proof certificates of employment terms. Secure tokenization facilitates seamless employment transactions, providing a clear and indisputable record of employment rights and obligations.
Building Trust Through Transparent Employment Transactions
One of the significant advantages of secure tokenized employment contracts is the transparency they bring to employment transactions. All stakeholders can trace the history of an employment contract, ensuring that terms are valid and in compliance. This transparency builds trust among parties involved in the employment process.
Efficiency in Employment Transactions
Secure tokenized employment contracts streamline the employment process, reducing administrative burdens and minimizing the risk of errors. With smart contracts automating tasks such as salary payments and employment renewals, stakeholders can engage in employment transactions with confidence, knowing that the process is efficient and secure.
Embracing the Future: Secure Tokenized Employment Contracts
As industries adapt to technological advancements, the adoption of secure tokenized employment contracts becomes a strategic move towards the future. These contracts promise enhanced security, transparency, and efficiency in employment transactions. To explore the transformative potential of secure tokenized employment contracts, visit