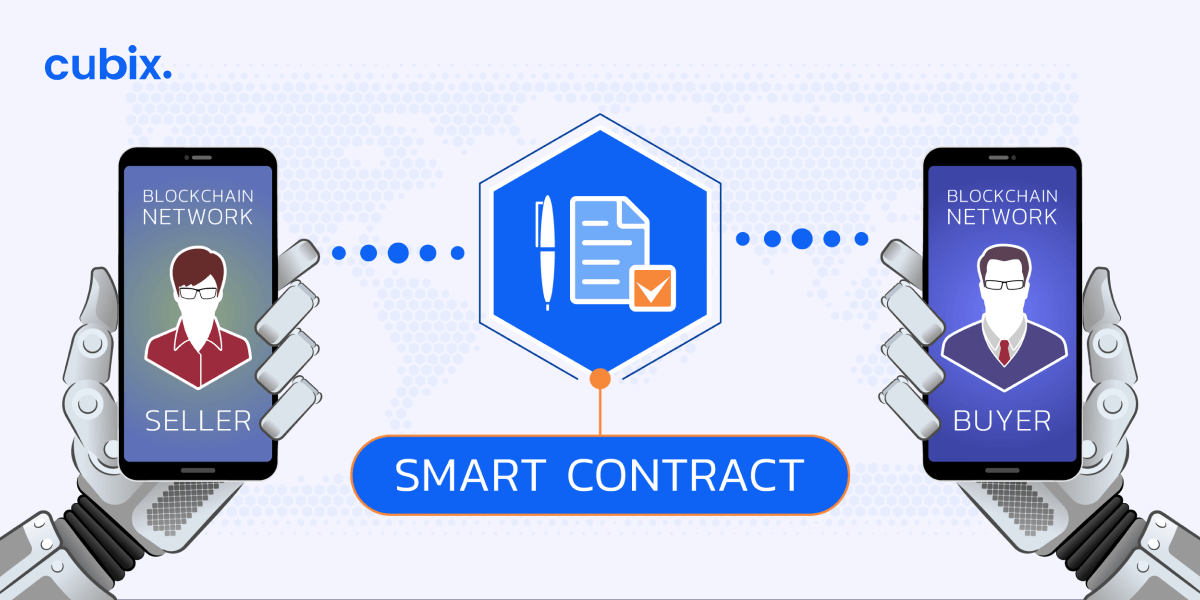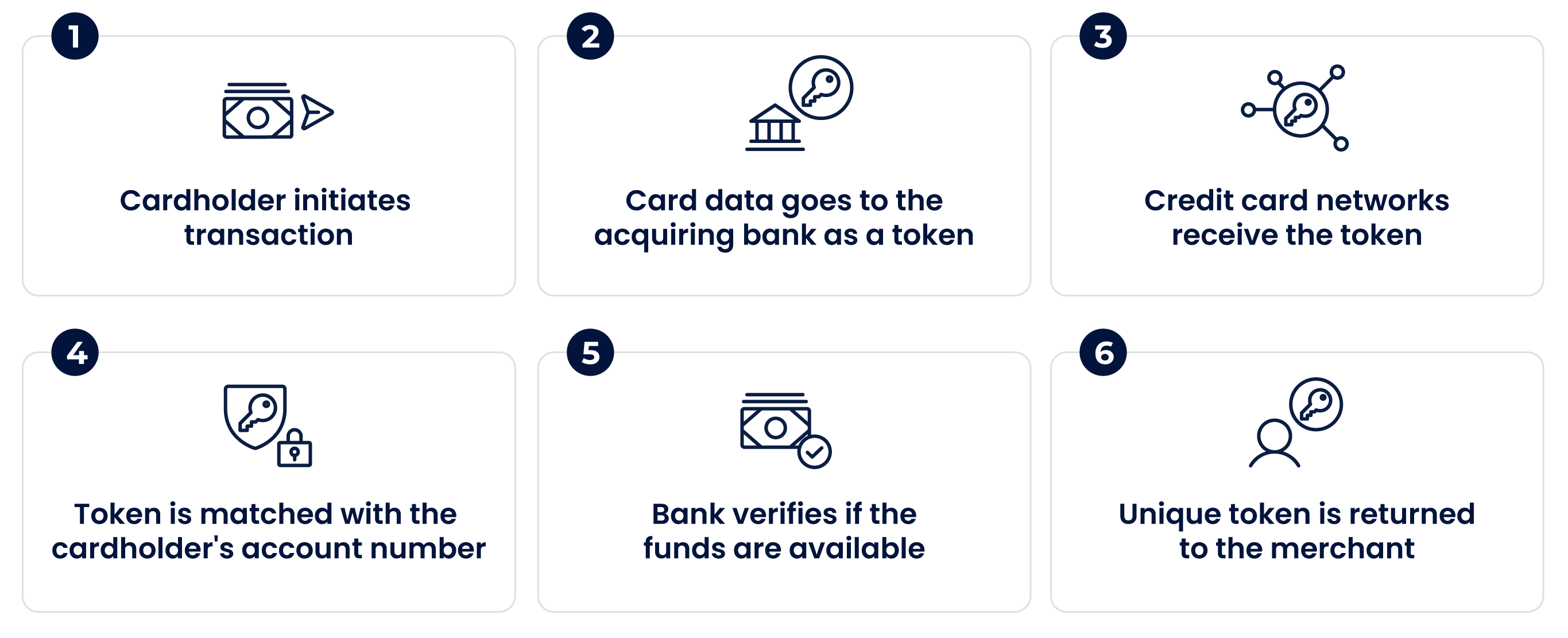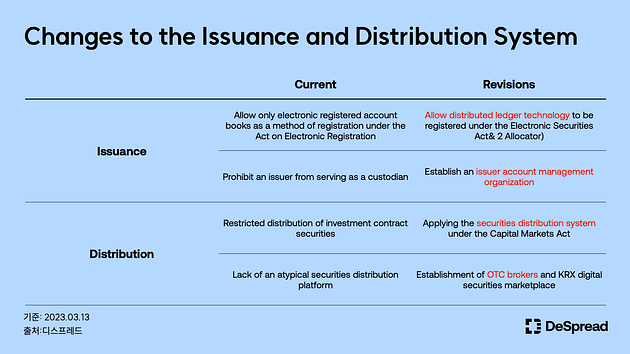
Issuing Secure Tokens: Enhancing Digital Authentication
The process of secure token issuance plays a pivotal role in modern digital authentication systems, ensuring the integrity and confidentiality of sensitive information. This article delves into the significance of secure token issuance, its mechanisms, applications, and the role it plays in fortifying digital security.
Understanding Secure Token Issuance
Secure token issuance involves the generation and distribution of unique tokens to users for authentication purposes. These tokens, often one-time-use codes or cryptographic keys, serve as a secondary layer of authentication beyond traditional passwords. The issuance process ensures that only authorized users can access protected systems or information.
Mechanisms Behind Secure Token Issuance
Various mechanisms contribute to the secure issuance of tokens. Time-based One-Time Passwords (TOTPs), where a dynamic code changes at regular intervals, and Hardware Security Tokens, physical devices generating secure codes, are common methods. Additionally, cryptographic algorithms may be employed to create unique tokens, enhancing the security of the issuance process.
Enhancing Two-Factor Authentication (2FA)
Secure token issuance is integral to the implementation of Two-Factor Authentication (2FA). By combining something the user knows (a password) with something the user has (a secure token), 2FA adds an extra layer of security. Even if passwords are compromised, unauthorized access is thwarted without the corresponding secure token.
Applications in Online Transactions
Secure token issuance finds extensive applications in securing online transactions. Banks and financial institutions often use secure tokens to provide an additional layer of protection for online banking activities. E-commerce platforms also leverage secure tokens to safeguard customer accounts during online purchases.
Mobile Authenticator Apps
Mobile authenticator apps are a popular medium for secure token issuance. These apps generate time-sensitive tokens directly on a user’s mobile device, eliminating the need for physical tokens or SMS-based codes. The convenience and portability of mobile authenticator apps contribute to their widespread adoption in various digital platforms.
Role in Identity and Access Management (IAM)
Secure token issuance is a fundamental component of Identity and Access Management (IAM) systems. IAM solutions use tokens to grant or deny access to resources based on user credentials. The issuance of secure tokens ensures that only authenticated users can access sensitive information or perform specific actions within an organization’s digital environment.
Mitigating the Risks of Phishing
Phishing attacks, where malicious actors attempt to trick users into revealing sensitive information, pose a significant threat. Secure token issuance mitigates these risks by adding an additional layer of authentication. Even if users unknowingly provide passwords through phishing, the lack of a corresponding secure token prevents unauthorized access.
Token Revocation and Expiry Policies
To maintain security, secure token issuance systems often implement token revocation and expiry policies. If a token is compromised or no longer needed, administrators can revoke or expire it. This proactive approach ensures that even if tokens fall into the wrong hands, they have a limited window of usability.
Adapting to Evolving Threats
As cyber threats continue to evolve, secure token issuance systems must adapt. Continuous monitoring, regular updates to encryption algorithms, and staying abreast