Revolutionizing Democracy: The Security of Tokenized Voting Contracts
In the realm of democratic processes, the integration of secure tokenized voting contracts is reshaping the way elections are conducted. This article explores the transformative impact of tokenized voting contracts, ushering in enhanced security, transparency, and integrity in electoral systems.
The Essence of Tokenization in Voting Contracts
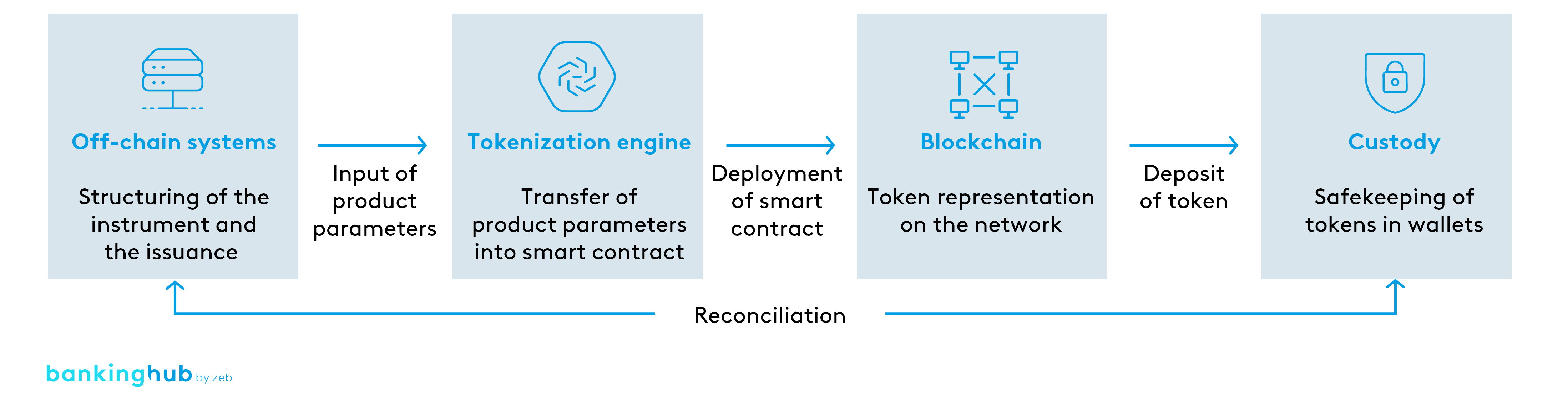
Tokenizing voting contracts involves representing the intricacies of voting processes digitally on a blockchain. This innovative approach simplifies the management of electoral agreements while introducing an unparalleled level of security through cryptographic measures. Each vote is encapsulated within a digital token, ensuring its uniqueness and protection.
Heightened Security Measures in Elections
Security is a fundamental concern in democratic elections, where the integrity of the voting process is paramount. Secure tokenized voting contracts utilize advanced cryptographic techniques to safeguard against tampering, fraud, and unauthorized access. This robust security layer enhances the trustworthiness of electoral outcomes.
Efficiency Gains in Voting Processes
Tokenized voting contracts streamline the entire voting process, from registration to ballot casting. The digitization of contracts allows for automated verification, reducing the potential for errors and ensuring the eligibility of voters. This efficiency not only accelerates the voting process but also enhances the overall integrity of elections.
Blockchain Integration for Transparency and Immutability
The integration of blockchain technology further fortifies the security of tokenized voting contracts. Blockchain’s decentralized and transparent nature ensures that all stakeholders involved in the electoral process have access to an immutable and tamper-resistant record of votes. This transparency builds trust and confidence in the democratic system.
To explore the potential of secure tokenized voting contracts, visit www.itcertswin.com.
Mitigating Risks in Electoral Processes
Democratic elections are susceptible to various risks, including voter fraud, manipulation, and disputes. Tokenized voting contracts provide a robust solution by creating an auditable and transparent trail of votes. This mitigates the risks associated with electoral malpractices and ensures the legitimacy of the democratic process.
Ensuring Voter Privacy and Anonymity
Tokenized voting contracts address concerns related to voter privacy and anonymity. The cryptographic nature of these contracts ensures that individual votes remain confidential while still contributing to the overall transparency of the election results. This balance between privacy and transparency is crucial for fostering trust in the electoral system.
Challenges and Solutions in Implementation
While the benefits of secure tokenized voting contracts are evident, their implementation faces challenges. Standardization, legal compliance, and widespread adoption require careful consideration. Collaborative efforts between technologists, policymakers, and electoral bodies are essential to overcoming these challenges and ensuring the success of tokenized voting systems.
Future Prospects: Innovations in E-Government
Looking ahead, the integration of emerging technologies in electronic government (e-government) holds promise for further optimizing the capabilities of tokenized voting contracts. Artificial intelligence, biometrics, and secure mobile applications are poised to enhance the accessibility, inclusivity, and security of electronic voting systems.
Empowering Citizens and Safeguarding Democracy
The adoption of secure tokenized voting contracts empowers citizens by ensuring the integrity of their votes. Additionally, it safeguards democracy by providing a resilient and secure