Revolutionizing Financial Transactions: The Security of Tokenized Investment Contracts
In the dynamic landscape of finance, the introduction of secure tokenized investment contracts is reshaping traditional approaches, bringing heightened security, transparency, and efficiency to the forefront of investment transactions.
Tokenization in Investment Contracts: A Digital Evolution
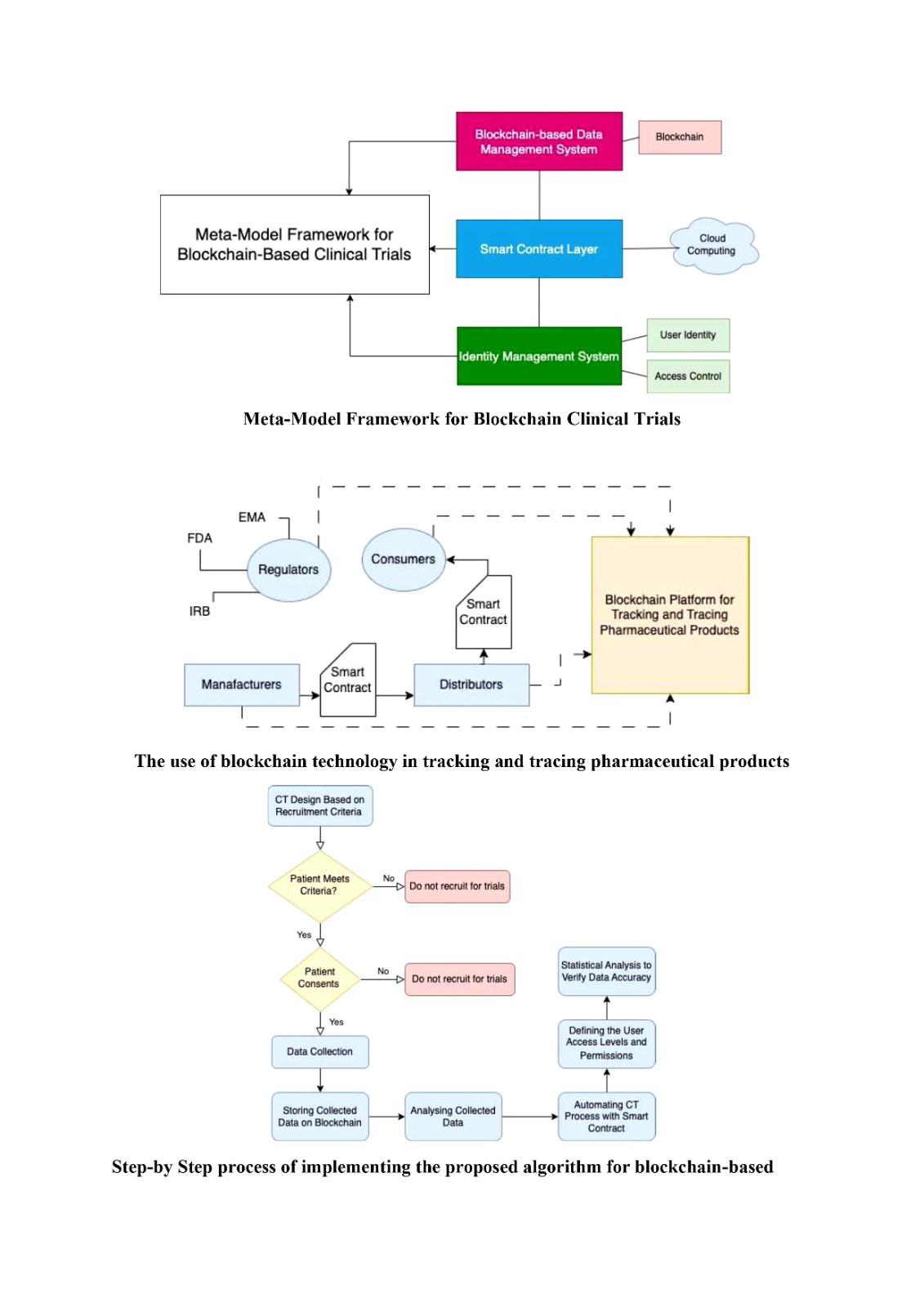
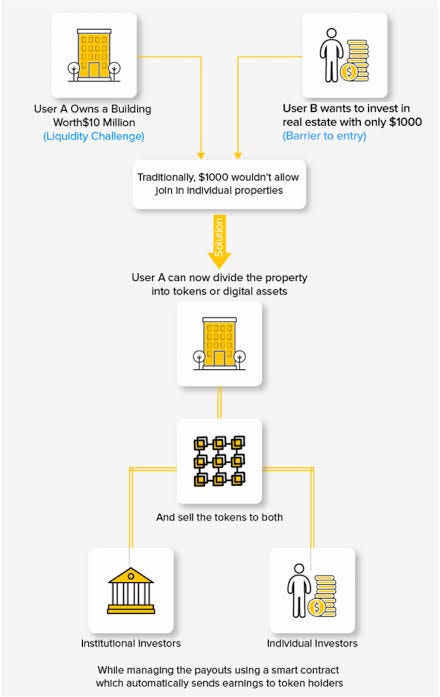
Tokenizing investment contracts involves representing ownership and transaction details digitally on a blockchain. This innovative process simplifies the management of investment transactions and introduces an unparalleled level of security through cryptographic measures. Each investment contract is uniquely represented by a digital token, ensuring transparency and protection.
Heightened Security Measures in Investment Transactions
Security is a paramount concern in the financial sector, where the value of investments can be substantial. Secure tokenized investment contracts leverage advanced cryptographic techniques to safeguard against unauthorized access, fraudulent activities, and illicit transactions. This robust security layer enhances the trustworthiness of investment transactions and the protection of investors’ assets.
Efficiency Gains in Investment Management
Tokenized investment contracts streamline the entire process of investment management, from ownership transfers to dividend distributions. The digitization of contracts allows for automated verification, reducing the potential for errors and ensuring the legitimacy of investment transactions. This efficiency not only accelerates investment processes but also enhances the overall integrity of the financial sector.
To explore the potential of secure tokenized investment contracts, visit www.itcertswin.com.
Blockchain Integration for Transparency and Accountability
The integration of blockchain technology further fortifies the security of tokenized investment contracts. Blockchain’s decentralized and transparent nature ensures that all stakeholders involved in financial transactions have access to an immutable and tamper-resistant record of ownership and transactions. This transparency builds trust and confidence in the authenticity of investment contracts.
Mitigating Risks in the Financial Sector
The financial sector is susceptible to various risks, including fraud, unauthorized transactions, and disputes over ownership. Tokenized investment contracts provide a robust solution by creating an auditable and transparent trail of transactions and ownership. This mitigates the risks associated with fraudulent activities and ensures the legitimacy of investment transactions.
Empowering Investors and Financial Institutions
Tokenized investment contracts play a pivotal role in empowering both investors and financial institutions. Investors benefit from increased transparency and confidence that their investments are secure and accurately managed. Financial institutions gain credibility through the transparent and accountable management of investment contracts, fostering trust among their clients.
Challenges and Solutions in Implementation
While the benefits of secure tokenized investment contracts are evident, their implementation faces challenges. Standardization, legal compliance, and integration with existing financial platforms require careful consideration. Collaborative efforts between financial institutions, blockchain developers, and legal experts are essential to overcoming these challenges and ensuring the success of tokenized investment contracts.
Future Prospects: Innovations in FinTech
Looking ahead, the integration of emerging technologies in finance holds promise for further optimizing the capabilities of tokenized investment contracts. Smart contracts, artificial intelligence, and decentralized applications are poised to enhance the investment experience, making financial transactions more accessible, transparent, and secure.
Building Trust in Financial Transactions
In conclusion, the integration of secure tokenized investment contracts marks a